Cyber Recovery, In the digital age, where organizations increasingly rely on interconnected systems and data-driven operations, cyber threats have grown both in scale and sophistication. As businesses and individuals face a constant barrage of attacks—ranging from ransomware to data breaches—cyber recovery has emerged as a critical element of a robust cybersecurity strategy. This article explores the concept of cyber recovery, its importance, and best practices for implementing an effective cyber recovery plan.
What is Cyber Recovery?
Cyber recovery refers to the process of restoring IT systems, networks, and data following a cyberattack or security breach. While cybersecurity focuses on preventing attacks, cyber recovery deals with the aftermath, ensuring that an organization can quickly return to normal operations with minimal data loss and downtime. In essence, it acts as the last line of defense when preventive measures fail.
Cyber recovery involves not only technical recovery but also business continuity planning. It emphasizes the need to restore critical business functions in a secure, resilient manner, which reduces the operational and financial impact of a cyber incident.
Why is Cyber Recovery Important?
The rise in cyberattacks—particularly ransomware—has underscored the need for organizations to prioritize cyber recovery. According to industry reports, the number of ransomware attacks surged dramatically in recent years, costing businesses millions of dollars in ransom payments, recovery efforts, and reputational damage. Even with top-tier security measures in place, there’s always a chance that an organization will be compromised. This is where a solid cyber recovery plan becomes crucial.
- Minimizing Downtime: When an organization is hit by a cyberattack, every minute of downtime can cost significant revenue. Cyber recovery ensures that businesses can restore their systems and get back online quickly, minimizing operational disruptions.
- Data Protection and Recovery: Data is the lifeblood of any modern organization. A well-prepared cyber recovery plan includes backups and redundant systems to recover lost or compromised data. This ensures business continuity and protects sensitive information from permanent loss.
- Compliance and Regulations: Many industries are subject to stringent data protection regulations, such as GDPR in Europe or HIPAA in the United States. A robust cyber recovery strategy helps ensure compliance with these regulations by protecting personal and sensitive information from being exposed in a breach.
- Preserving Business Reputation: Cyberattacks can cause irreparable harm to a company’s reputation. The ability to recover quickly and efficiently demonstrates resilience and can help maintain trust with customers, partners, and stakeholders.
Key Elements of a Cyber Recovery Plan
Developing a comprehensive cyber recovery plan requires careful consideration of several key elements:
- Regular Data Backups: The cornerstone of any cyber recovery strategy is regular, secure backups of critical data. Backups should be stored in offsite locations or in cloud environments that are isolated from the main network to ensure they aren’t compromised during an attack.
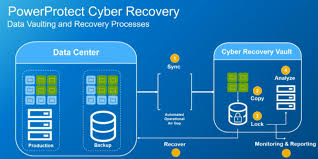
- Isolation of Critical Systems: A cyber recovery vault or isolated recovery environment (IRE) can protect critical systems and data from cyber threats. These vaults operate independently from the primary network, making them less vulnerable to attack and providing a clean, secure environment from which to restore operations.
- Incident Response Plan: Having a well-defined incident response plan is essential to handling cyberattacks. This plan should outline roles, responsibilities, communication strategies, and procedures for responding to different types of cyber incidents.
- Regular Testing and Drills: It’s not enough to have a cyber recovery plan; it must be regularly tested to ensure its effectiveness. Conducting drills and simulations helps organizations identify weaknesses and refine their recovery processes.
- Cyber Insurance: While cyber recovery plans help minimize losses, cyber insurance can provide financial protection against some of the costs associated with recovery, including legal fees, regulatory fines, and the cost of restoring systems.
- Collaboration with Third-Party Experts: Engaging third-party cybersecurity experts and managed security service providers (MSSPs) can bolster an organization’s cyber recovery efforts. These experts can provide additional support in the event of an attack and help ensure a swift recovery.
Emerging Trends in Cyber Recovery
As cyber threats evolve, so too must cyber recovery strategies. Several trends are shaping the future of cyber recovery:
- Automation: Automated recovery solutions are gaining traction as they allow organizations to respond to incidents faster and with fewer human errors. These tools can detect anomalies, isolate affected systems, and initiate recovery processes with minimal manual intervention.
- AI and Machine Learning: AI and machine learning are being integrated into cyber recovery processes to help predict and respond to threats more effectively. These technologies analyze vast amounts of data to identify patterns, enabling quicker detection of threats and more precise recovery efforts.
- Zero Trust Architecture: The Zero Trust model, which assumes that no one inside or outside the network is automatically trusted, is becoming a cornerstone of cybersecurity. In terms of cyber recovery, this means ensuring that access to critical recovery systems is tightly controlled, limiting the risk of further breaches during recovery efforts.
- Cloud-Based Recovery Solutions: As more businesses move to the cloud, cloud-based recovery solutions are becoming increasingly popular. These solutions offer scalability, flexibility, and cost-efficiency, allowing organizations to quickly restore data and applications from the cloud following an attack.
Conclusion
In today’s cyber threat landscape, having a robust cyber recovery plan is no longer optional—it’s a necessity. With the right combination of preventative measures and recovery strategies, businesses can mitigate the damage caused by cyberattacks, ensuring that they can resume operations quickly and with minimal disruption. By investing in regular backups, isolation techniques, and cutting-edge technologies like automation and AI, organizations can stay resilient in the face of growing cyber threats.
You Might Also Like These:
Dell Technologies Cyber Recovery: A Comprehensive Solution for Modern Cybersecurity Threats
Christopher Mullen and the Cyber Addiction Recovery Center: Pioneering Digital Wellness
Why Is Recovery Planning Needed for Cybersecurity?
2018 Cyber Security: Disaster Recovery Planning and YouTube’s Role
Recovery Planning After a Cyber Attack: A Crucial Guide for Businesses