Power Protect Cyber Recovery Solution, In today’s rapidly evolving digital landscape, cyber threats are a constant concern for organizations of all sizes. With data breaches, ransomware attacks, and malicious activities on the rise, companies must implement advanced strategies to safeguard their critical information. One solution that has emerged as a powerful defense against these threats is the PowerProtect Cyber Recovery Solution. Developed by Dell Technologies, this cutting-edge tool is designed to help businesses protect, isolate, and recover their data in the event of a cyberattack.
What is Power Protect Cyber Recovery Solution?
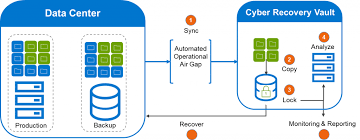
The PowerProtect Cyber Recovery Solution is an advanced data protection tool that offers a unique approach to cybersecurity and data recovery. Unlike traditional backup solutions, which may become compromised during a cyberattack, PowerProtect focuses on isolating critical data, ensuring that it remains safe from unauthorized access. The solution provides organizations with a dedicated cyber recovery vault, where critical data is stored in an immutable state, protecting it from ransomware, malware, or other forms of cyber threats.
Key Features of Power Protect Cyber Recovery Solution
- Data Isolation: PowerProtect creates an isolated environment—commonly referred to as a “cyber recovery vault”—that is physically and logically separated from the primary network. This vault acts as a secure enclave where sensitive data is kept safe from potential attackers.
- Immutable Storage: One of the key components of the PowerProtect solution is the use of immutable storage. Data stored in the vault cannot be altered or deleted once written, making it resilient against ransomware encryption or manipulation.
- Automated Recovery Workflows: In the event of an attack, PowerProtect provides automated recovery workflows that guide organizations through the data restoration process. This ensures faster recovery times and minimizes downtime, allowing businesses to get back to normal operations quickly.
- Analytics and Forensics: PowerProtect Cyber Recovery Solution leverages advanced analytics to continuously monitor data integrity. It also provides forensic tools to help organizations investigate the cause of an attack, identifying potential vulnerabilities.
- Compliance and Governance: For industries with stringent regulatory requirements, the solution offers capabilities that help businesses remain compliant with data protection laws and standards. PowerProtect helps organizations maintain audit trails and data logs, ensuring that recovery processes are well-documented.
How Power Protect Cyber Recovery Works
The PowerProtect Cyber Recovery Solution operates in three main stages: isolation, integrity, and recovery.
- Isolation: The first step is isolating the data in a secure, air-gapped environment. This ensures that even if the primary network is compromised, the critical data remains untouched.
- Integrity: In the integrity phase, PowerProtect continuously monitors and verifies the integrity of the data within the vault. If any anomalies or threats are detected, alerts are sent out to the security team for immediate action.
- Recovery: When a cyberattack occurs, and the primary data becomes compromised, the recovery phase begins. PowerProtect’s automated workflows allow for the quick restoration of clean data, ensuring minimal disruption to business operations.
Why Businesses Need Power Protect Cyber Recovery Solution
The growing sophistication of cyber threats means that traditional backup and disaster recovery solutions are no longer sufficient. Ransomware attacks, for example, have increased dramatically, with attackers targeting not only live systems but also backups. Once these backups are compromised, organizations may find themselves with no clean data to restore. PowerProtect Cyber Recovery Solution addresses this by isolating critical data, ensuring it remains untouched and recoverable.
Here are some reasons why organizations should consider Power Protect:
- Protection Against Ransomware: With ransomware attacks becoming more frequent, PowerProtect ensures that critical data is stored securely in an immutable format, preventing attackers from encrypting or deleting it.
- Rapid Recovery: The automated recovery processes minimize downtime, allowing organizations to quickly restore operations after a cyberattack.
- Enhanced Security: By creating an isolated cyber recovery vault, PowerProtect reduces the risk of data breaches and ensures that sensitive information remains protected.
- Cost Efficiency: While the cost of a cyberattack can be devastating, the proactive use of PowerProtect Cyber Recovery Solution helps reduce the financial impact by enabling quick recovery and minimizing business disruption.
Conclusion
As cyber threats continue to evolve, businesses must adopt more sophisticated tools to protect their data. The PowerProtect Cyber Recovery Solution provides a comprehensive defense against the growing menace of ransomware and other cyberattacks. With its robust features, including data isolation, immutable storage, and automated recovery workflows, PowerProtect helps organizations safeguard their most critical asset: their data. By investing in this solution, companies can ensure they are well-prepared to face the ever-changing threat landscape and recover swiftly in the event of a cyberattack.
The Power Protect Cyber Recovery Solution is a vital tool for modern businesses, ensuring that they remain resilient and protected in the face of evolving cyber threats.
You Might Also Like These:
The Importance of a Cyber Disaster Recovery Plan Template
Christopher Mullen’s Cyber Addiction Recovery Center: A Beacon of Hope for the Digital Age
What Is the Main Purpose of Cyber Incident Recovery?
Cyber Incident Management and Recovery Plan: A Strategic Approach to Resilience
2018 Cyber Security: Disaster Recovery Planning and YouTube’s Role