Dell Cyber Recovery Vault, In today’s digital landscape, organizations face a growing number of cyber threats that are becoming more sophisticated and damaging. Ransomware, malware, and targeted cyberattacks can bring business operations to a halt, disrupt services, and lead to significant financial and reputational loss. To address these threats, Dell Technologies offers a robust solution: the Dell Cyber Recovery Vault. This article explores how the Cyber Recovery Vault works and why it’s an essential tool for protecting critical business data.
What is Dell Cyber Recovery Vault?
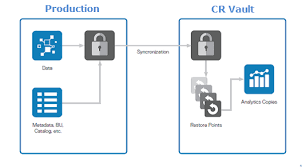
The Dell Cyber Recovery Vault is a secure, isolated environment designed to safeguard an organization’s most critical data from cyberattacks. It acts as a final line of defense by separating backup data from the operational environment, ensuring that in the event of an attack, your essential data remains intact and uncompromised. Unlike traditional backup solutions, the Cyber Recovery Vault provides an additional layer of protection by physically and logically isolating data, making it inaccessible to attackers.
How Dell Cyber Recovery Vault Works
- Data Isolation and Air Gap:
The Cyber Recovery Vault is physically and logically separated from the production network, creating an “air gap” that limits access to the stored data. This isolation ensures that even if a cyberattack compromises the primary network, the vault remains untouched. The air gap is activated during replication windows, ensuring that only authorized and secure replication processes are allowed. - Immutable Data Copies:
Data stored in the Dell Cyber Recovery Vault is immutable, meaning it cannot be altered, deleted, or encrypted by attackers. Once a backup is placed inside the vault, it becomes locked, protecting it from unauthorized changes. This immutability is critical in defending against ransomware, which typically targets backups as part of its destructive process. - Automated and Secure Recovery:
In the event of a cyberattack, organizations need to recover their critical data quickly to restore business operations. Dell’s Cyber Recovery Vault enables rapid recovery by ensuring that the last known clean copy of your data is readily available. The system also uses automation and orchestration tools to streamline the recovery process, reducing downtime and helping businesses get back on their feet faster. - Cybersecurity Analytics and Anomaly Detection:
The Dell Cyber Recovery Vault incorporates advanced analytics and machine learning to detect any anomalies in the stored data. By monitoring data integrity and scanning for suspicious behavior, the vault can detect early signs of corruption or cyber threats. If any irregularities are found, it triggers alerts, allowing IT teams to investigate and take action before any damage is done. - Compliance and Governance:
Many industries, such as finance and healthcare, are subject to strict regulatory requirements regarding data protection and recovery. The Dell Cyber Recovery Vault helps organizations meet compliance standards by ensuring that critical data is stored securely and can be retrieved efficiently in the event of a breach. The system also provides detailed audit logs and reporting features to simplify the compliance process.
Key Benefits of Dell Cyber Recovery Vault
- Enhanced Security: The vault’s isolation and immutability provide a significant security advantage, making it almost impossible for attackers to compromise backup data.
- Operational Efficiency: Automated recovery processes reduce the time and complexity involved in restoring operations after a cyber incident, minimizing downtime.
- Proactive Threat Detection: With built-in anomaly detection and cyber analytics, organizations can identify and address potential threats before they lead to data loss or business disruption.
- Scalability: The Cyber Recovery Vault can be tailored to fit organizations of all sizes and industries, providing flexible storage options that can grow with the business.
- Regulatory Compliance: The solution simplifies adherence to industry regulations by providing a secure, auditable system for data storage and recovery.
Why Dell Cyber Recovery Vault Matters
As the frequency and severity of cyberattacks continue to rise, organizations must take proactive steps to protect their most valuable asset: data. While traditional security measures like firewalls and antivirus software are essential, they are no longer sufficient on their own. A cyber recovery strategy that includes a solution like the Dell Cyber Recovery Vault is crucial for ensuring that businesses can withstand and recover from attacks quickly.
The importance of having an isolated, secure backup system cannot be overstated. The Dell Cyber Recovery Vault provides peace of mind, knowing that your critical data is protected even if other layers of security fail. This added layer of protection helps mitigate the risks associated with evolving cyber threats and gives organizations a fighting chance to recover their data without paying ransoms or facing extended downtime.
Conclusion
In the battle against modern cyber threats, the Dell Cyber Recovery Vault stands as a powerful tool for ensuring data protection and business continuity. By isolating backup data, making it immutable, and integrating advanced threat detection, Dell’s solution goes beyond traditional backup systems to offer a robust and secure recovery plan. For any organization looking to strengthen its cybersecurity posture, the Dell Cyber Recovery Vault is a crucial asset that provides an extra layer of defense against the ever-evolving landscape of cybercrime.
You Might Also Like These:
Cyber Security Recovery Images: Essential Tools for Data Protection and Recovery
Cyber Recovery Plan for a New Business Area: A Comprehensive Guide
Creating a Comprehensive Cyber Security Disaster Recovery Plan: An Infographic Guide
Ponemon Institute: Insights on Cyber Security Attack Recovery
Cyber Workplace Recovery Services, LIC: Ensuring Business Continuity in the Digital Age