Dell Emc Cyber Recovery, In today’s digital age, businesses and organizations face an increasing number of cyber threats, ranging from ransomware to insider attacks. To mitigate these risks, robust data protection strategies are essential. Among the most advanced solutions available is Dell EMC Cyber Recovery, designed specifically to protect and recover critical data in the event of a cyber attack.
The Need for Cyber Recovery
As cyber threats grow more sophisticated, traditional backup and disaster recovery solutions often fall short in protecting against advanced cyber-attacks. Many cybercriminals target backups and critical data, crippling businesses by preventing them from restoring their systems. This is where Dell EMC Cyber Recovery comes in as a critical addition to an organization’s data protection strategy.
What is Dell EMC Cyber Recovery?
Dell EMC Cyber Recovery is a comprehensive solution designed to provide an additional layer of security for an organization’s most critical data. It focuses on isolating backup data in a secure, air-gapped environment and ensures that this data remains protected from any potential cyber threats.
The solution includes:
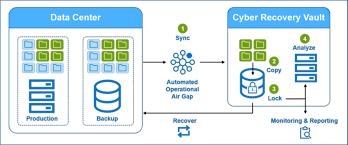
- Air-Gapped Vault: One of the standout features of Dell EMC Cyber Recovery is the creation of an isolated, secure vault. This vault is completely separate from the organization’s primary network, ensuring that in the event of a cyber attack, the critical data stored in this vault is unaffected.
- Automated Workflow: Cyber Recovery automates the process of moving critical data into the vault, streamlining data protection. The workflow includes identifying sensitive data, copying it to the vault, and verifying its integrity.
- Immutable Copies: Immutable data copies ensure that once the data is stored, it cannot be altered or deleted, which is crucial in preventing ransomware or insider threats from tampering with backups.
- Analytics and Forensic Tools: The solution also integrates with forensic analysis tools that help organizations detect any anomalies or threats within their backup data, providing early warnings of potential issues.
How Dell EMC Cyber Recovery Works
Dell EMC Cyber Recovery operates through a well-defined, multi-step process designed to provide a comprehensive level of protection for sensitive data:
- Data Isolation: Critical business data is regularly copied and isolated in a cyber vault. This vault is air-gapped from the main production environment, effectively cutting it off from unauthorized access.
- Data Integrity: Using advanced analytics, Dell EMC Cyber Recovery continually monitors the integrity of the vault’s contents, ensuring that any malicious activity is detected early.
- Recovery Planning: The solution allows organizations to create cyber recovery policies and workflows to ensure they can quickly recover from an attack. This involves verifying data integrity, conducting test restores, and automating recovery processes.
- Post-Attack Recovery: In the event of a cyber attack, the data stored in the isolated vault remains unaffected. The organization can then use the preserved copies to restore their systems, minimizing downtime and data loss.
Benefits of Dell EMC Cyber Recovery
1. Enhanced Security with Isolation
The air-gapped vault is the cornerstone of Dell EMC Cyber Recovery, offering a level of data protection that traditional backup solutions cannot provide. By isolating critical data from the production environment, it eliminates the possibility of external threats accessing this information.
2. Reduced Recovery Time
In the event of a cyber attack, the faster an organization can recover, the less damage it will experience. Dell EMC Cyber Recovery significantly reduces recovery time by providing immediate access to clean data copies, allowing businesses to resume operations faster.
3. Proactive Threat Detection
With advanced analytics integrated into the solution, organizations can detect threats and vulnerabilities within their backup data before they evolve into full-scale attacks. This proactive approach reduces the risk of data corruption and ensures that only clean data is available for recovery.
4. Compliance and Audit Readiness
For industries with strict regulatory requirements around data security and retention, Dell EMC Cyber Recovery helps organizations meet compliance standards. The solution ensures that data is stored securely and can be audited at any time, making it easier to satisfy legal obligations.
5. Scalable for Any Environment
Whether it’s a small business or a large enterprise, Dell EMC Cyber Recovery is designed to scale and adapt to different IT environments. This flexibility ensures that any organization can benefit from the solution, regardless of size or industry.
Conclusion
In a world where cyber threats are becoming more pervasive and dangerous, organizations must adopt a proactive approach to data protection. Dell EMC Cyber Recovery offers a powerful and comprehensive solution for safeguarding critical business data by isolating it from cyber threats, ensuring rapid recovery in case of an attack, and providing the tools to proactively detect potential issues. By investing in such a solution, businesses can protect their most valuable asset—their data—and ensure long-term operational resilience.
You Might Also Like These:
Cyber Recovery Air Gap: A Critical Defense Against Cyber Threats
The Importance of Cyber Security and Disaster Recovery: Designing an Effective Logo
Understanding ICS Cyber Attack Recovery Time: Key Factors and Best Practices