Disater Recovery Program Cyber Security, In today’s digital age, businesses and organizations are heavily reliant on data and technology for their operations. This dependency makes them vulnerable to various cyber threats, including data breaches, ransomware, and natural disasters that could disrupt their systems. A Disaster Recovery Program (DRP) in cybersecurity is a critical component that ensures organizations can quickly recover from these incidents and resume normal operations without significant losses.
In this article, we explore the significance of disaster recovery programs in cybersecurity, why they are essential, and the steps involved in developing an effective recovery plan.
What is a Disaster Recovery Program?
A disaster recovery program is a set of documented policies and procedures that help an organization recover critical systems and data after a cyber incident or other catastrophic events. In the context of cybersecurity, it is specifically focused on ensuring the availability and integrity of data, systems, and networks, reducing downtime, and limiting the damage caused by a security breach or other disruptive events.
Types of Disasters Addressed by a DRP in Cybersecurity
- Cyber Attacks: These include malware, ransomware, denial-of-service attacks (DDoS), and other hacking attempts that can disable a company’s IT infrastructure.
- Data Breaches: Unauthorized access to sensitive information could lead to significant financial and reputational losses.
- Natural Disasters: Events like floods, hurricanes, and earthquakes that can physically damage data centers or other IT infrastructure.
- Human Errors: Mistakes such as accidental deletion of critical files or misconfigurations of systems can lead to significant data loss.
- System Failures: Hardware malfunctions, software bugs, or network outages can cripple an organization’s ability to function.
The Role of Cybersecurity in a Disaster Recovery Program
Cybersecurity and disaster recovery are closely intertwined. While cybersecurity measures aim to prevent attacks, a disaster recovery program ensures that an organization can recover if an attack occurs despite its defenses. A robust DRP ensures that the following elements are prioritized:
- Data Backup and Recovery: Ensuring regular backups of all critical data, both on-site and off-site, is vital. Encrypted backups provide an added layer of security in the event of a breach.
- Incident Response: The DRP should include detailed instructions on how to respond to specific cyber incidents. This helps in quick identification and containment of threats, minimizing further damage.
- Business Continuity: Disaster recovery is a key part of business continuity planning (BCP), which ensures that essential services remain operational even in the wake of a cyber incident.
- Security Testing and Updates: Routine security audits and updates are integral to ensuring the disaster recovery program stays effective. Testing recovery strategies through drills and simulations ensures that teams are prepared for real-world scenarios.
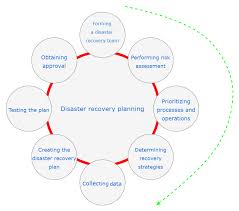
Steps to Develop an Effective Disaster Recovery Program for Cybersecurity
Creating a comprehensive disaster recovery plan is an essential investment for any organization. Here’s a step-by-step guide to developing an effective disaster recovery program with a focus on cybersecurity:
1. Risk Assessment
The first step is identifying potential risks, including cyber threats, hardware failures, and natural disasters. This assessment helps prioritize which systems and data need the most protection.
2. Set Recovery Objectives
Two critical objectives should be defined:
- Recovery Time Objective (RTO): The maximum acceptable amount of downtime that an organization can tolerate.
- Recovery Point Objective (RPO): The maximum acceptable amount of data loss measured in time. This determines how often data backups need to be performed.
3. Develop a Data Backup Strategy
A key aspect of any disaster recovery plan is ensuring that backups are performed regularly and stored securely. Automated backups, combined with encryption and off-site storage, provide a reliable safety net in the event of an attack.
4. Establish an Incident Response Plan
Clearly outline the steps to be taken immediately after a cyber incident is detected. This should include a communication plan, identifying stakeholders and response teams, as well as detailed instructions for system isolation and forensic analysis.
5. Test and Maintain the DRP
Testing is essential to ensure that the recovery plan works effectively. Conduct regular disaster recovery drills, update the plan with new technology or business processes, and review it periodically to ensure that it remains current.
Benefits of a Disaster Recovery Program in Cybersecurity
An effective disaster recovery program offers numerous advantages:
- Minimized Downtime: A well-structured DRP ensures that systems and data are restored quickly, reducing the amount of downtime an organization experiences after a disaster.
- Reduced Financial Losses: The faster an organization can recover from a cyber attack, the lower the potential losses. Downtime and data loss can cost millions, and a DRP helps mitigate these risks.
- Data Protection and Compliance: Many industries require adherence to strict regulatory guidelines regarding data protection. A DRP ensures that organizations comply with these requirements, avoiding fines and penalties.
- Increased Customer Trust: Businesses that can quickly recover from cyber incidents tend to maintain higher levels of customer trust. Consumers are more likely to stay loyal to organizations that demonstrate resilience against cyber threats.
Conclusion
A disaster recovery program in cybersecurity is not just a precautionary measure; it’s a critical strategy for protecting an organization’s data, reputation, and financial well-being. As cyber threats continue to evolve, organizations must stay proactive, preparing for the worst while securing themselves against potential attacks. By investing in a well-designed DRP, businesses can ensure that they are ready to face any disruption with minimal impact, safeguarding their long-term success.
Implementing a disaster recovery program may seem complex, but it is a vital element of any comprehensive cybersecurity strategy.
You Might Also Like These:
Digimon Story: Cyber Sleuth Bug Recovery
Mimecast: 365 Days of Data Recovery and Cyber Resilience
Multi Recovery DX in Cyber Sleuth: Reviving Your Digital Experienc
Cyber-State Recovery: Navigating the Path to Digital Resilience
Sample Cyber Security Disaster Recovery Plan: A Blueprint for Resilience
Sample Cyber Security Disaster Recovery Plan: A Blueprint for Resilience