Cyber Incident Management Recovery Planning, In today’s digitally-driven world, organizations face an increasing number of cyber threats, ranging from ransomware attacks to data breaches. Cyber incident management recovery planning is crucial for businesses to not only withstand these threats but also to recover swiftly and effectively. This article will delve into the essential components of cyber incident management recovery planning, outlining steps organizations can take to minimize damage and restore operations.
Understanding Cyber Incident Management
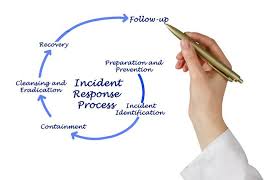
Cyber incident management involves a systematic approach to handling cyber threats and breaches. This includes preparation, detection, response, recovery, and learning from incidents. A robust recovery plan is vital, as it helps organizations minimize downtime, protect sensitive data, and maintain trust with customers and stakeholders.
Key Components of Cyber Incident Management Recovery Planning
- Risk Assessment and Analysis
Organizations should begin by conducting a thorough risk assessment to identify vulnerabilities within their systems. This analysis should include evaluating the potential impact of various cyber incidents and the likelihood of their occurrence. Understanding these risks is crucial for prioritizing resources and crafting an effective recovery plan. - Incident Response Team (IRT)
Establishing a dedicated incident response team is essential. This team should consist of members from various departments, including IT, legal, communications, and management. Their role is to coordinate responses during a cyber incident and ensure that recovery efforts are executed efficiently. - Developing a Cyber Incident Response Plan (CIRP)
A comprehensive CIRP outlines the specific steps to take during a cyber incident. This plan should include:- Identification of Critical Assets: Knowing which systems and data are vital for operations allows for focused protection and quicker recovery.
- Communication Protocols: Establish clear channels for internal and external communication. This includes notifying stakeholders, customers, and law enforcement when necessary.
- Containment Strategies: Implement procedures to isolate affected systems and prevent the spread of the incident.
- Testing and Simulation
Regularly testing the incident response plan through simulations can help identify gaps and improve the team’s response time. Tabletop exercises allow the incident response team to practice their roles and refine their strategies in a controlled environment. - Data Backup and Recovery
Frequent backups are a cornerstone of recovery planning. Organizations should ensure that they have reliable and secure data backup solutions in place, allowing for quick restoration of services. It’s essential to test these backups regularly to confirm their integrity. - Post-Incident Review
After managing a cyber incident, conducting a post-incident review is vital for continuous improvement. This review should assess what went well, what didn’t, and how the organization can enhance its incident response strategies in the future.
The Importance of Cyber Incident Management Recovery Planning
Effective cyber incident management recovery planning is critical for several reasons:
- Minimized Downtime: A well-prepared organization can recover faster, reducing the impact on business operations.
- Cost Savings: The financial implications of cyber incidents can be significant. A solid recovery plan can mitigate these costs by enabling quick restoration of services.
- Regulatory Compliance: Many industries have regulations regarding data protection and breach notifications. Effective recovery planning ensures compliance and helps avoid potential fines.
- Enhanced Reputation: Organizations that can demonstrate resilience in the face of cyber threats are likely to maintain customer trust and loyalty.
Conclusion
In an era where cyber threats are ever-evolving, cyber incident management recovery planning is not just a best practice; it’s a necessity. By taking proactive steps to assess risks, establish a response team, develop a comprehensive plan, and continually improve through testing and reviews, organizations can better protect themselves against cyber incidents. Investing in effective recovery planning ultimately safeguards not just the organization’s data and operations, but also its reputation and bottom line.
You Might Also Like These:
Understanding Operant Conditioning and Spontaneous Recovery in Cyber Rats
Power Protect Cyber Recovery: A Comprehensive Solution for Modern Data Protection
Dell Cyber Recovery Solution: A Comprehensive Approach to Data Protection
IT Firms That Specialize in Cyber Attack Recovery: A Critical Line of Defense
Cyber Rat Spontaneous Recovery: Understanding Resilience in Digital Systems