Dellemc Cyber Recovery, In today’s digital landscape, where cyber threats are increasingly sophisticated and pervasive, organizations must prioritize their data protection strategies. One solution gaining traction is Dell EMC Cyber Recovery, which offers a comprehensive approach to safeguarding critical business data against cyberattacks.
Understanding Dell EMC Cyber Recovery
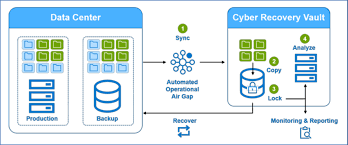
Dell EMC Cyber Recovery is an advanced data protection solution designed to help organizations defend against ransomware and other cyber threats. This solution utilizes a unique architecture that separates backup data from the production environment, ensuring that even if an organization is compromised, their backup data remains secure and intact.
Key Features of Dell EMC Cyber Recovery
- Isolation of Backup Data: One of the standout features of Dell EMC Cyber Recovery is its ability to isolate backup data. By keeping backup copies in a secure environment, organizations can prevent attackers from accessing and encrypting their backups during an attack.
- Automated Workflows: The solution includes automated workflows for backup, recovery, and monitoring, which streamline processes and reduce the chances of human error. This automation helps organizations respond more quickly and effectively in the event of a cyber incident.
- Advanced Threat Detection: Dell EMC Cyber Recovery integrates advanced analytics and monitoring tools to detect potential threats before they can cause significant damage. This proactive approach enables organizations to act swiftly to mitigate risks.
- Comprehensive Reporting and Compliance: Organizations can generate detailed reports on their backup and recovery processes, which not only aids in internal audits but also helps ensure compliance with regulatory requirements. This feature is crucial for businesses operating in regulated industries.
- Scalability and Flexibility: Dell EMC Cyber Recovery is designed to grow with your organization. Whether you’re a small business or a large enterprise, the solution can be tailored to meet your specific needs, making it a versatile choice for any organization.
Benefits of Implementing Dell EMC Cyber Recovery
- Enhanced Data Security: By ensuring that backup data is isolated and protected, organizations can significantly reduce their vulnerability to ransomware and other cyber threats.
- Rapid Recovery: In the event of a cyberattack, Dell EMC Cyber Recovery enables organizations to restore their operations quickly. This rapid recovery minimizes downtime and helps maintain business continuity.
- Peace of Mind: Knowing that your data is secure and easily recoverable allows businesses to focus on growth and innovation rather than worrying about potential cyber threats.
- Cost-Effective Solution: The long-term cost savings associated with reduced downtime and data loss can far outweigh the initial investment in Dell EMC Cyber Recovery.
Conclusion
In an era where cyber threats are a constant concern, Dell EMC Cyber Recovery offers organizations a robust solution to protect their data and ensure business continuity. By isolating backup data, automating recovery processes, and providing advanced threat detection, this solution empowers businesses to navigate the complexities of today’s cyber landscape confidently. Implementing Dell EMC Cyber Recovery not only enhances data security but also fosters resilience, allowing organizations to thrive in a challenging environment.
For businesses looking to bolster their cybersecurity measures, Dell EMC Cyber Recovery is a strategic investment that can safeguard against the unpredictable nature of cyber threats
You Might Also Like These:
The Importance of a Cyber Recovery Plan: Safeguarding Your Business in the Digital Age
Disaster Recovery in Cybersecurity: A Comprehensive Guide to Safeguarding Digital Assets
Cyber Recovery and Addiction: Navigating Alcohol Recovery in the Digital Age
PowerProtect Cyber Recovery Solution: A Comprehensive Guide to Ensuring Data Security
Cyber Rat Extinction and Spontaneous Recovery: A Tale of Digital Evolution