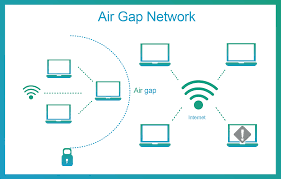
Cyber Recovery Air Gap, In today’s digital landscape, organizations are increasingly reliant on technology to store and manage their data. However, with the rise of cyber threats such as ransomware attacks and data breaches, ensuring the security and integrity of that data has become more crucial than ever. One effective strategy that organizations are adopting to protect their critical data is the concept of a cyber recovery air gap.
Understanding Cyber Recovery Air Gap
A cyber recovery air gap is a security measure designed to create a physical or logical separation between a primary network and a backup network or data repository. This separation ensures that in the event of a cyber attack, especially ransomware, the backup data remains inaccessible and unaffected. Essentially, an air gap acts as a protective barrier, isolating critical data from potential threats.
How It Works
The implementation of a cyber recovery air gap typically involves the following components:
- Isolated Backup Systems: Organizations maintain a separate backup environment that is not connected to the internet or the primary network. This could involve using offline storage devices or a secondary data center that is physically disconnected.
- Regular Data Backups: Backups are performed on a scheduled basis, ensuring that the most recent data is captured. These backups can be stored on various mediums, such as tapes, external hard drives, or cloud storage solutions that are not continuously connected to the primary environment.
- Access Controls: Strict access controls are implemented to ensure that only authorized personnel can access the backup environment. This minimizes the risk of insider threats and unauthorized access.
- Testing and Verification: Regular testing of the backup systems is essential to ensure that data can be restored quickly and effectively in the event of an incident. Verification processes help confirm that backups are intact and free from corruption.
Benefits of Cyber Recovery Air Gap
- Protection Against Ransomware: One of the primary advantages of implementing a cyber recovery air gap is its effectiveness against ransomware attacks. In the event that the primary network is compromised, the isolated backup remains unaffected, allowing for recovery without the need to pay a ransom.
- Data Integrity: By keeping backup data isolated, organizations can ensure the integrity of their critical data. This is particularly important for industries that handle sensitive information, such as finance, healthcare, and government.
- Regulatory Compliance: Many industries are subject to strict regulations regarding data protection and privacy. Implementing a cyber recovery air gap can help organizations comply with these regulations by ensuring that backup data is secure and easily recoverable.
- Disaster Recovery: In addition to protecting against cyber threats, a cyber recovery air gap can also enhance an organization’s disaster recovery capabilities. Whether due to natural disasters, hardware failures, or cyber incidents, having a secure backup allows for a more robust recovery plan.
Challenges and Considerations
While the benefits of a cyber recovery air gap are significant, organizations must also consider some challenges:
- Cost: Implementing an air gap solution can involve significant investment in infrastructure and resources, particularly for smaller organizations with limited budgets.
- Operational Complexity: Maintaining a separate backup environment requires careful planning and ongoing management to ensure that backups are performed regularly and accurately.
- Recovery Time: Depending on the recovery process and the amount of data that needs to be restored, the recovery time can be longer than desired, especially when relying on physical media.
Conclusion
In an era where cyber threats are a constant concern, organizations must take proactive steps to protect their data. A cyber recovery air gap provides a valuable layer of security, ensuring that critical backups remain safe from malicious attacks. By understanding the principles behind this strategy and implementing it effectively, organizations can significantly enhance their resilience against cyber threats, safeguarding their data and maintaining business continuity in the face of adversity.
You Might Also Like These:
Recovery After Cyber Radiation on Breast: A Comprehensive Guide
Disaster Recovery in Cyber Security: A Critical Component of Resilience
The Rise of Cyber Addiction and the Role of Cyber Addiction Recovery Centers
Cyber Disaster Recovery in Florida: A Crucial Strategy for Business Resilience
Length of Recovery from a Cyber Attack: What Businesses Should Expect