Dell EMC Cyber Recovery IBM Services Cyber Vault, In today’s increasingly digital landscape, organizations face constant threats to their critical data, systems, and IT infrastructure. The rise in cyberattacks like ransomware, data breaches, and other sophisticated threats has put immense pressure on businesses to secure their information assets. As a response to this, leading technology companies are developing innovative solutions to protect against these attacks. Two such solutions are Dell EMC Cyber Recovery and IBM Services Cyber Vault, each offering a robust strategy to enhance cybersecurity resilience.
The Rising Importance of Cyber Recovery
Cyber recovery has become a priority for organizations because traditional disaster recovery methods, while essential, may not be sufficient to address the growing risks associated with cybercrime. Unlike natural disasters or hardware failures, cyberattacks are often targeted, adaptive, and highly sophisticated. They can leave companies vulnerable to prolonged downtime, massive financial losses, and reputational damage.
Dell EMC has recognized the growing need for specialized solutions that protect businesses against such attacks. Their Cyber Recovery solution stands as a pillar of their data protection and cybersecurity offerings.
Dell EMC Cyber Recovery: A Proactive Defense
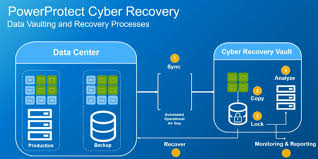
Dell EMC Cyber Recovery is a solution designed to help organizations protect, isolate, and recover their critical data in the event of a cyberattack. Its approach goes beyond traditional backup solutions by focusing on proactive defense and recovery capabilities that address cyber threats.
Key features of Dell EMC Cyber Recovery include:
- Data Isolation: One of the core elements of this solution is its ability to create an air-gapped environment. This isolation ensures that critical data is stored in a secure vault that is separate from the production environment, reducing the risk of ransomware or malware spreading from affected systems.
- Immutable Data Copies: By maintaining immutable copies of critical data, Dell EMC ensures that organizations can recover unaltered versions of their data after a breach. These copies are time-locked and cannot be modified, offering a trustworthy recovery point.
- Analytics and Threat Detection: Dell EMC Cyber Recovery is integrated with advanced analytics and threat detection tools that help identify abnormal behavior and potential cyber threats within the recovery environment. This feature enables organizations to detect potential breaches before they can cause further damage.
- Orchestrated Recovery: After identifying and mitigating the threat, businesses can use the orchestrated recovery feature to bring systems back online efficiently. Dell EMC’s solution ensures that data is restored securely and that normal operations can resume quickly after a cyber incident.
Dell EMC Cyber Recovery provides a layered defense against cyberattacks, giving businesses the assurance that their most critical assets are protected and recoverable.
IBM Services Cyber Vault: Enhancing Cyber Resilience
IBM, a global leader in IT services and cybersecurity, offers a complementary solution through its Cyber Vault services. The Cyber Vault is an advanced approach to safeguarding critical business data by creating a secured, isolated environment that is equipped to protect against cyberattacks, particularly ransomware.
Some key features of IBM Services Cyber Vault include:
- Proactive Risk Mitigation: Like Dell EMC’s Cyber Recovery, IBM’s Cyber Vault focuses on isolating critical data in a secured, air-gapped environment. This reduces the risk of an attacker compromising both the production and backup systems simultaneously, allowing for clean recovery options.
- Automated Backup and Recovery: IBM’s Cyber Vault continuously monitors and automates backup operations to ensure that data remains protected at all times. With automatic backups, organizations reduce the risk of human error and ensure that critical information is always recoverable.
- Advanced Analytics and Intelligence: IBM integrates cutting-edge analytics tools into its Cyber Vault services. These tools monitor the data environment for irregularities and potential threats, providing early warning signs of a possible cyberattack.
- Recovery Orchestration and Testing: Recovery is an integral part of IBM’s service offering. The company provides recovery orchestration tools that allow businesses to quickly and effectively restore their operations after an attack. IBM also offers testing capabilities so organizations can simulate various attack scenarios and ensure their recovery strategies are robust.
- Cyber Recovery as a Service: IBM extends its Cyber Vault capabilities through a managed service model, allowing businesses to leverage their expertise in cybersecurity without managing the infrastructure themselves. This is particularly useful for organizations lacking in-house cybersecurity resources.
Integrating Dell EMC Cyber Recovery with IBM Cyber Vault for Comprehensive Protection
While both Dell EMC and IBM offer powerful cyber recovery solutions independently, they can also work in tandem to create a comprehensive cybersecurity strategy. Organizations with complex infrastructures or those looking for an additional layer of protection may choose to integrate these solutions for enhanced defense.
For example, businesses can use Dell EMC Cyber Recovery for managing isolated backups and immutable data storage, while relying on IBM’s Cyber Vault for proactive threat detection and recovery orchestration. By combining the strengths of these two industry leaders, companies can build a multi-layered, defense-in-depth strategy that not only safeguards their data but also ensures swift recovery in the event of an attack.
Conclusion
As cyber threats continue to evolve, so too must the strategies to counter them. Dell EMC Cyber Recovery and IBM Services Cyber Vault represent two of the most advanced solutions available today for protecting critical data and ensuring business continuity in the face of cyberattacks. Both solutions offer unique strengths in isolation, analytics, and recovery orchestration, making them invaluable to modern enterprises looking to bolster their cyber resilience.
Incorporating both Dell EMC and IBM’s technologies can provide organizations with the comprehensive protection they need to not only defend against cyber threats but to recover swiftly and effectively when attacks occur. Investing in these solutions is not just about safeguarding data—it’s about ensuring the long-term survival and success of the business in an ever-connected, digital world.
You Might Also Like These:
Understanding Forex Fraud: How to Protect Yourself
Is Forex Trading Fraud? Understanding the Risks and Realities
Understanding Forex Trading Fraud: How to Protect Yourself