What Is The Main Purpose Of Cyber Incident Recovery, In today’s digital landscape, organizations face a constant threat from cyber incidents, which can range from data breaches and ransomware attacks to insider threats and system failures. As cyberattacks become more frequent and sophisticated, businesses must have a plan in place to respond swiftly and effectively. One crucial aspect of this response strategy is cyber incident recovery. But what is the main purpose of cyber incident recovery, and why is it so critical for organizations?
Understanding Cyber Incident Recovery
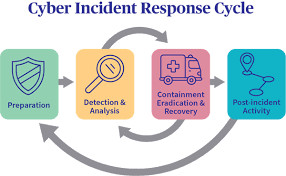
Cyber incident recovery refers to the processes and actions taken by an organization to restore normal operations following a cyber incident. It involves a combination of technical, managerial, and strategic steps that aim to minimize the damage caused by the incident, repair affected systems, and ensure that operations are restored to a normal state as quickly as possible. This recovery process is a key part of a broader cybersecurity framework, often working in tandem with incident detection, response, and prevention.
The Main Purpose of Cyber Incident Recovery
The main purpose of cyber incident recovery is to restore critical business functions and minimize downtime. While this sounds simple, the process involves several layers of complexity. Here’s why this purpose is essential:
- Business Continuity: The primary goal of any business is to maintain operations. Cyber incidents can severely disrupt the ability to function, from halting customer transactions to causing a loss of sensitive data. Recovery ensures that the business can return to normalcy with minimal interruptions, preserving revenue, customer trust, and operational stability.
- Minimizing Damage: Every minute that systems remain compromised can lead to greater damage, whether in terms of lost data, breached customer information, or financial loss. Effective recovery helps contain and mitigate these impacts, reducing the long-term effects on the organization.
- Restoring Data Integrity and Security: Cyber incidents can compromise data, leading to corruption, loss, or exposure of sensitive information. A key part of the recovery process is to ensure that data is restored accurately, securely, and completely, minimizing the risk of future vulnerabilities stemming from the attack.
- Compliance with Regulations: Many industries are subject to strict data protection regulations, such as GDPR, HIPAA, or PCI-DSS, that mandate timely incident reporting and recovery. Failure to recover from an incident promptly can result in hefty fines, legal consequences, and reputational damage. Cyber incident recovery helps ensure compliance with these legal obligations.
- Preserving Customer Trust: Data breaches or system failures can erode customer trust, especially if personal or financial information is compromised. A quick and efficient recovery, paired with transparent communication, can help reassure customers that the situation is under control, reducing the likelihood of reputational harm.
- Reducing Financial Impact: Cyber incidents can be costly, not just in terms of lost revenue, but also in recovery efforts, legal liabilities, and regulatory penalties. Effective cyber incident recovery can help reduce these financial losses by bringing systems back online swiftly and preventing further damage.
Key Steps in Cyber Incident Recovery
To achieve its main purpose, a well-structured cyber incident recovery plan typically involves the following steps:
- Assessing the Damage: The first step is to evaluate the extent of the damage caused by the incident, including identifying affected systems, data loss, and security vulnerabilities.
- Containment and Mitigation: Once the damage is assessed, the next step is to contain the incident. This may involve isolating affected systems, shutting down compromised networks, or applying security patches to prevent further spread.
- Recovery of Systems and Data: After containment, the focus shifts to restoring systems and recovering lost or corrupted data. This may include restoring backups, repairing databases, or reinstalling compromised software.
- Testing and Validation: Once systems are restored, thorough testing must be conducted to ensure that everything is functioning properly, and that no further vulnerabilities exist.
- Documentation and Review: Finally, it’s essential to document the recovery process, including lessons learned and actions taken. This helps improve future incident response and recovery strategies.
Conclusion
The main purpose of cyber incident recovery is to restore business functions and minimize downtime while reducing the impact of a cyberattack on operations, data integrity, and organizational reputation. As cyber threats continue to evolve, having an effective recovery plan in place is crucial for businesses to bounce back quickly from incidents and safeguard their future resilience. In a world where cyber risks are a part of everyday operations, recovery is not just about getting back to business—it’s about ensuring the long-term sustainability and trustworthiness of the organization.
You Might Also Like These:
cyber attack disaster recovery plan template
cyber security recovery plan template