Dell Technolgies Cyber Recovery, In today’s interconnected digital world, businesses are constantly under the looming threat of cyberattacks. With the increasing sophistication of cybercriminals and the evolution of malware, ransomware, and other malicious attacks, organizations must prioritize protecting their critical data and IT infrastructure. Dell Technologies has emerged as a leader in this space, offering a robust solution known as Dell Technologies Cyber Recovery to mitigate these growing risks.
Understanding the Cybersecurity Landscape
Cyberattacks have become a daily occurrence for organizations worldwide. From data breaches to ransomware attacks, the costs — both financial and reputational — can be immense. The 2023 Global Risks Report by the World Economic Forum highlighted that cyber threats are one of the top risks faced by businesses today. In response to these challenges, companies are investing heavily in cybersecurity solutions that not only prevent attacks but also ensure rapid recovery after incidents.
However, traditional backup and recovery methods often fall short in dealing with advanced threats like ransomware. Modern cyberattacks are not just about stealing data; they involve encryption, manipulation, and deliberate destruction of backups, leaving companies with no way to restore their systems.
This is where Dell Technologies Cyber Recovery comes into play — offering a comprehensive solution that focuses on the recovery aspect of cyber resilience.
What is Dell Technologies Cyber Recovery?
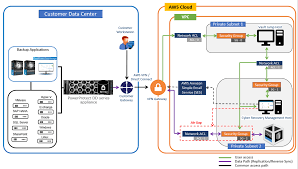
Dell Technologies Cyber Recovery is a specialized solution designed to protect and isolate critical data in the event of a cyberattack. Its goal is to ensure that even if an organization’s main systems are compromised, there is a secure and untouchable copy of the essential data that can be restored quickly and efficiently.
Key components of Dell Technologies Cyber Recovery include:
- Isolated Data Vault: Unlike traditional backup systems, Cyber Recovery creates an isolated environment (known as a “vault”) that is separate from the main network. This vault is highly secure and inaccessible by hackers, ensuring that backup data remains safe even during an active cyberattack.
- Automated Data Management: The solution automates the process of moving data into the isolated vault, ensuring that only clean, verified data enters. This reduces the chances of compromised or malicious files contaminating the vault environment.
- Immutable Copies of Data: Cyber Recovery creates immutable, unchangeable copies of critical data. This ensures that data cannot be modified or deleted by either external attackers or internal users.
- Advanced Analytics: One of the standout features of Dell Technologies Cyber Recovery is its use of machine learning and advanced analytics to continuously monitor the data in the vault. This helps detect anomalies that could indicate a security threat, allowing organizations to respond proactively before it becomes a full-blown disaster.
- Orchestration for Quick Recovery: Should a cyberattack occur, organizations can rely on Dell Technologies Cyber Recovery’s orchestrated workflows to restore operations quickly. This minimizes downtime and helps businesses get back on their feet faster.
Why is Dell Technologies Cyber Recovery Essential?
- Ransomware Protection: The rise of ransomware has led to a significant demand for solutions that ensure business continuity after an attack. Dell Technologies Cyber Recovery addresses this by ensuring that even if ransomware locks down an organization’s primary systems, the isolated vault remains safe and unaffected. Organizations can restore their systems from this clean backup without having to pay ransom demands.
- Compliance and Regulatory Requirements: Many industries, such as healthcare and finance, are governed by strict data protection regulations. Cyber Recovery helps businesses stay compliant by ensuring that sensitive data is protected and recoverable, even in the face of a cyberattack.
- Long-Term Cost Savings: While the upfront investment in a cyber recovery solution may seem high, the long-term cost savings are significant. The potential financial losses from extended downtime, lost data, and reputational damage far outweigh the cost of implementing Dell Technologies Cyber Recovery.
- Cyber Resilience: Organizations are moving beyond traditional cybersecurity models that focus solely on prevention. Instead, they are adopting a more holistic approach known as cyber resilience, which includes the ability to recover quickly after a breach. Dell Technologies Cyber Recovery is a key part of this strategy, ensuring that companies can restore operations quickly and efficiently.
Conclusion
As cyber threats continue to evolve, businesses must adopt advanced strategies that go beyond prevention. Dell Technologies Cyber Recovery offers a robust solution designed to secure critical data, isolate it from threats, and ensure rapid recovery in the event of an attack. With its automated workflows, advanced analytics, and immutable backup systems, Dell Technologies Cyber Recovery empowers organizations to face the modern threat landscape with confidence.
Investing in a comprehensive cyber recovery solution is no longer optional — it’s essential for protecting your business from the ever-growing risks of cyberattacks. Dell Technologies has positioned itself as a leader in this field, providing the tools and infrastructure needed to ensure your organization’s resilience in the digital age.
You Might Also Like These:
cyber security disaster recovery plan template