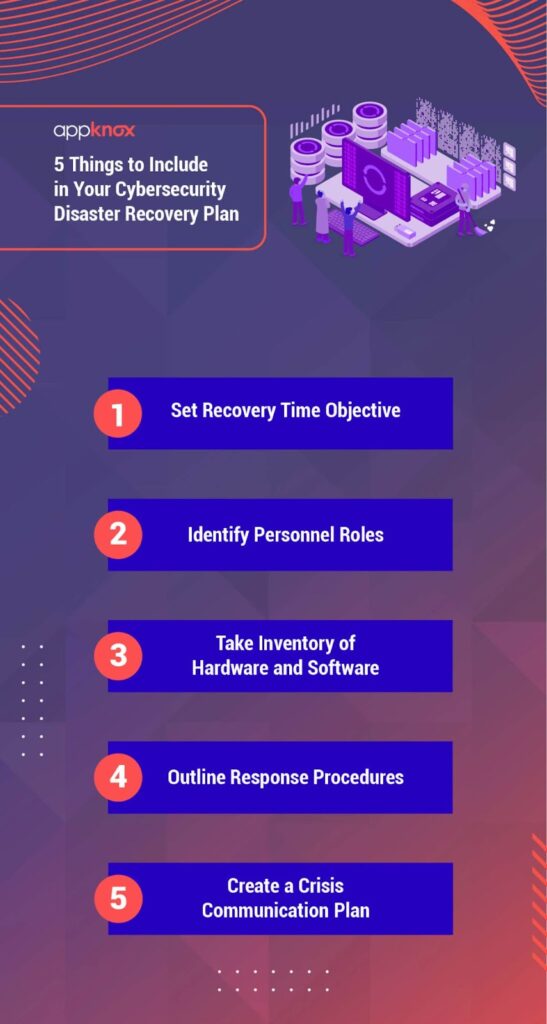
Sample Cyber Attack Recovery Plan, In today’s digital landscape, cyber threats are an ever-present danger for organizations of all sizes. A well-structured recovery plan is essential for mitigating the impact of a cyber attack. This article outlines a sample cyber attack recovery plan, detailing the key components that organizations should consider to ensure a swift and effective response.
Understanding Cyber Attack Recovery
A cyber attack recovery plan is a strategic framework designed to help organizations respond to and recover from cyber incidents. This plan should encompass processes for identifying, containing, and recovering from a breach, minimizing disruption to business operations, and protecting sensitive data.
Key Components of a Cyber Attack Recovery Plan
1. Preparation
Preparation is the foundation of a successful recovery plan. Organizations should invest in the following areas:
- Risk Assessment: Regularly conduct risk assessments to identify vulnerabilities in your IT infrastructure.
- Security Policies: Establish robust security policies that include data encryption, access controls, and employee training.
- Backup Solutions: Implement reliable backup solutions to ensure data can be restored quickly and effectively in the event of a breach.
2. Detection and Identification
The first step in recovery is to detect and identify the attack. Organizations should:
- Monitor Systems: Use security information and event management (SIEM) tools to monitor network traffic and detect anomalies.
- Incident Reporting: Establish a clear incident reporting process for employees to notify the IT department of any suspicious activity.
3. Containment
Once a breach is detected, it’s crucial to contain the attack to prevent further damage. Steps to take include:
- Isolate Affected Systems: Disconnect compromised systems from the network to limit the spread of the attack.
- Identify Attack Vectors: Determine how the breach occurred to address the underlying vulnerabilities.
4. Eradication
After containment, the next step is to eradicate the threat. This involves:
- Remove Malicious Software: Utilize antivirus and malware removal tools to eliminate threats from affected systems.
- Patch Vulnerabilities: Apply patches and updates to software and systems to prevent future attacks.
5. Recovery
Recovery is the process of restoring systems to normal operation. Key actions include:
- Restore Data: Use backups to restore lost or compromised data.
- System Testing: Conduct thorough testing of restored systems to ensure they are functioning correctly and are secure.
6. Communication
Effective communication during a cyber attack is vital. Organizations should:
- Internal Communication: Keep all relevant internal stakeholders informed about the status of the attack and recovery efforts.
- External Communication: Prepare a statement for clients and partners, informing them of the incident and the steps being taken to resolve it.
7. Post-Incident Analysis
Once recovery is complete, organizations should conduct a post-incident analysis to evaluate the response:
- Debriefing: Hold a debriefing session with the response team to discuss what worked well and what could be improved.
- Update the Plan: Revise the cyber attack recovery plan based on lessons learned to enhance future responses.
8. Regular Testing and Drills
To ensure that the recovery plan remains effective, organizations should conduct regular testing and drills:
- Simulation Exercises: Run tabletop exercises to simulate a cyber attack and practice the recovery plan.
- Continuous Improvement: Use feedback from drills to continually refine and improve the recovery strategy.
Conclusion
A sample cyber attack recovery plan is a critical component of an organization’s cybersecurity strategy. By preparing for potential incidents, organizations can significantly reduce the impact of cyber attacks and ensure a swift recovery. Regular updates and testing of the recovery plan will help organizations stay ahead of evolving threats in the digital landscape. Implementing these strategies not only protects sensitive data but also fosters trust among clients and stakeholders, ensuring business continuity in an increasingly complex cyber environment.
You Might Also Like These: