Cyber Incident Response And Recovery, In today’s digital landscape, organizations face a constant barrage of cyber threats that can compromise sensitive data, disrupt operations, and damage reputations. As cyber attacks become more sophisticated, having an effective cyber incident response and recovery strategy is essential for organizations to mitigate risks and ensure business continuity. This article delves into the importance of cyber incident response and recovery, outlining the key components and best practices to enhance an organization’s resilience against cyber threats.
Understanding Cyber Incident Response
Cyber incident response refers to the structured approach that organizations take to prepare for, detect, and respond to cyber incidents. The goal is to effectively manage the aftermath of a security breach or cyber attack to limit damage and reduce recovery time and costs. A well-defined incident response plan is critical for minimizing the impact of an incident and restoring normal operations as quickly as possible.
Key Phases of Incident Response
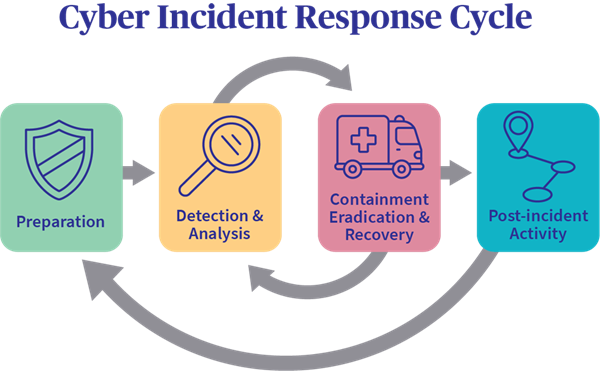
- Preparation: This phase involves developing an incident response plan, training team members, and establishing communication protocols. Organizations should also implement security measures and conduct regular security assessments to identify potential vulnerabilities.
- Detection and Analysis: Rapid detection of security incidents is vital. This phase includes monitoring systems for unusual activity, analyzing alerts, and determining the nature and scope of the incident. Effective detection relies on advanced security tools and technologies, as well as trained personnel.
- Containment, Eradication, and Recovery: Once an incident is confirmed, it’s crucial to contain the breach to prevent further damage. This may involve isolating affected systems, removing malicious software, and securing vulnerabilities. After containment, organizations must work to restore systems and services while ensuring that the threat has been completely eradicated.
- Post-Incident Activity: After recovery, organizations should conduct a thorough review of the incident to understand what happened and how to prevent future occurrences. This phase includes updating incident response plans, documenting lessons learned, and conducting additional training if necessary.
The Importance of Recovery
Recovery is a critical component of the incident response process. It involves restoring affected systems and data to their normal operational state. A strong recovery plan not only focuses on technical recovery but also considers the emotional and operational impact on employees and stakeholders.
Strategies for Effective Recovery
- Data Backup and Restoration: Regularly backing up data is essential for recovery. Organizations should implement a robust backup strategy that includes off-site storage and regular testing of backup systems to ensure data integrity.
- Business Continuity Planning: A business continuity plan outlines how an organization will continue to operate during and after a cyber incident. This includes identifying critical functions, personnel roles, and communication strategies to maintain operations.
- Communication and Support: During recovery, clear communication is essential. Organizations should keep all stakeholders informed about the status of recovery efforts, expected timelines, and any changes to operations. Providing support to employees during this period can also help maintain morale and productivity.
- Testing and Drills: Regularly testing incident response and recovery plans through drills can help organizations identify weaknesses and improve their overall readiness. These exercises should simulate real-world scenarios to provide valuable insights into the effectiveness of current strategies.
Best Practices for Cyber Incident Response and Recovery
- Establish an Incident Response Team: Form a dedicated team responsible for incident response activities, including representation from IT, legal, HR, and public relations.
- Develop Clear Policies and Procedures: Create well-documented policies and procedures for incident detection, reporting, and response to ensure that all employees understand their roles.
- Invest in Security Technologies: Utilize advanced security tools, such as intrusion detection systems and security information and event management (SIEM) solutions, to enhance monitoring and detection capabilities.
- Engage with External Experts: In the event of a significant cyber incident, it may be beneficial to engage external cybersecurity experts who can provide additional support and expertise.
- Learn and Adapt: Cyber threats are continually evolving, making it vital for organizations to stay informed about the latest trends and best practices. Regularly update incident response plans based on new threats and lessons learned from past incidents.
Conclusion
The increasing frequency and complexity of cyber incidents make it imperative for organizations to prioritize cyber incident response and recovery. By investing in comprehensive response strategies and fostering a culture of security awareness, organizations can significantly enhance their resilience against cyber threats. A proactive approach not only protects valuable assets but also builds trust with customers and stakeholders, ultimately ensuring long-term success in an ever-evolving digital landscape.
You Might Also Like These:
information security training army alms