Cyber Response Recovery, In today’s digital landscape, the threat of cyberattacks is an ever-present concern for organizations of all sizes. As cybercriminals become more sophisticated, the need for effective cyber response recovery strategies has never been more critical. This article explores the importance of cyber response recovery and outlines best practices to enhance an organization’s resilience against cyber threats.
Understanding Cyber Response Recovery
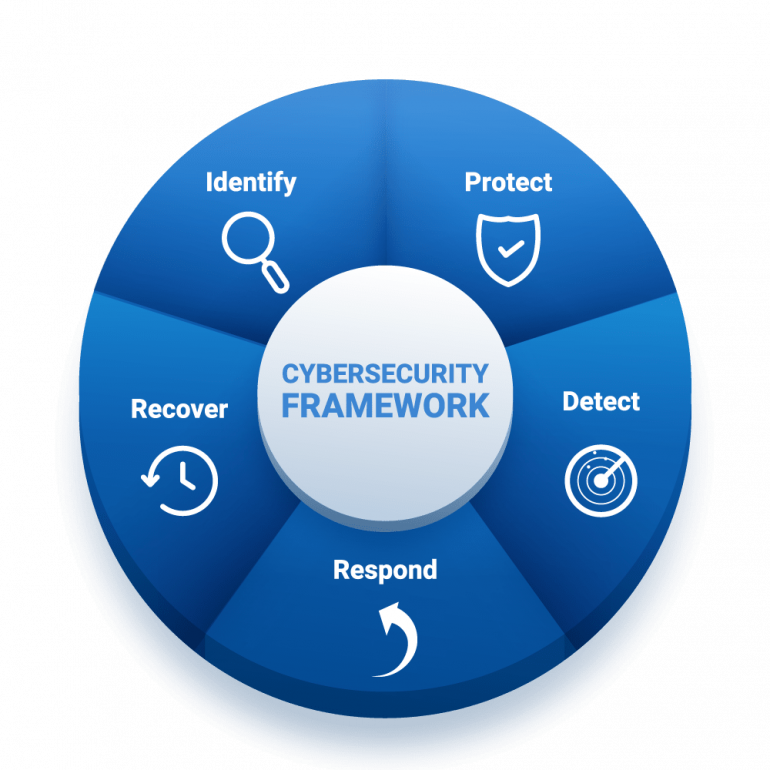
Cyber response recovery refers to the systematic approach an organization takes to recover from a cyber incident. This includes the steps necessary to restore systems and data, assess the impact of the incident, and implement measures to prevent future occurrences. Effective recovery not only minimizes downtime but also helps organizations maintain trust with customers and stakeholders.
The Importance of Cyber Response Recovery
- Minimizing Downtime: Cyberattacks can lead to significant operational disruptions. A well-defined recovery strategy helps organizations resume normal operations as quickly as possible, reducing financial losses.
- Data Integrity and Protection: Recovery processes ensure that data is restored accurately and securely. This is crucial for maintaining the integrity of sensitive information and meeting regulatory compliance.
- Reputation Management: A swift and effective recovery can mitigate damage to an organization’s reputation. Customers are more likely to remain loyal to a business that handles incidents transparently and responsibly.
- Continuous Improvement: Each cyber incident provides valuable insights. A robust recovery strategy includes post-incident analysis, allowing organizations to learn from their experiences and enhance their cybersecurity posture.
Key Components of a Cyber Response Recovery Plan
- Preparation: Organizations should develop a comprehensive incident response plan that outlines roles, responsibilities, and procedures. Regular training and simulations help ensure that staff are prepared for potential cyber incidents.
- Detection and Analysis: Early detection is critical for effective recovery. Implementing advanced monitoring tools can help identify breaches quickly. Analyzing the incident to understand its nature and scope is essential for an effective response.
- Containment: Once an incident is detected, immediate containment measures must be taken to prevent further damage. This may involve isolating affected systems, blocking malicious traffic, or disabling compromised accounts.
- Eradication: After containing the threat, organizations should focus on eradicating the root cause of the incident. This may include removing malware, closing vulnerabilities, and applying patches to affected systems.
- Recovery: The recovery phase involves restoring systems and data from backups, ensuring that operations can resume. It’s crucial to verify that systems are secure before bringing them back online.
- Post-Incident Review: After recovery, organizations should conduct a thorough review of the incident. This includes assessing the effectiveness of the response, identifying lessons learned, and updating the incident response plan accordingly.
Best Practices for Cyber Response Recovery
- Regular Backups: Ensure that data is backed up regularly and that backups are stored securely. This is vital for quick recovery in the event of a ransomware attack or data loss.
- Invest in Cybersecurity Tools: Utilizing advanced cybersecurity solutions, such as intrusion detection systems and endpoint protection, can enhance an organization’s ability to detect and respond to threats.
- Engage with Experts: Consider partnering with cybersecurity experts or consultants who can provide guidance on developing and implementing an effective cyber response recovery plan.
- Educate Employees: Regular training on cybersecurity awareness can empower employees to recognize potential threats and respond appropriately, significantly reducing the risk of incidents.
- Test and Update the Plan: Regularly test the cyber response recovery plan through simulations and drills. This helps identify gaps in the strategy and ensures that the team is familiar with their roles during a real incident.
Conclusion
Cyber response recovery is a critical component of an organization’s overall cybersecurity strategy. By developing a robust recovery plan and implementing best practices, organizations can enhance their resilience against cyber threats. In an increasingly digital world, proactive measures in cyber response recovery not only protect an organization’s assets but also safeguard its reputation and trust with stakeholders. As cyber threats evolve, so too must the strategies to combat them, ensuring that organizations are prepared to respond and recover effectively.
You Might Also Like These:
cyber attack disaster recovery plan template
cyber security recovery plan sample