Recovery Planning Cyber Security, In an increasingly digital world, where cyber threats loom larger than ever, organizations must prioritize their cybersecurity strategies. One of the most critical aspects of these strategies is recovery planning. Effective recovery planning in cybersecurity ensures that businesses can swiftly return to normal operations following a cyber incident, minimizing damage and restoring trust.
Understanding Recovery Planning
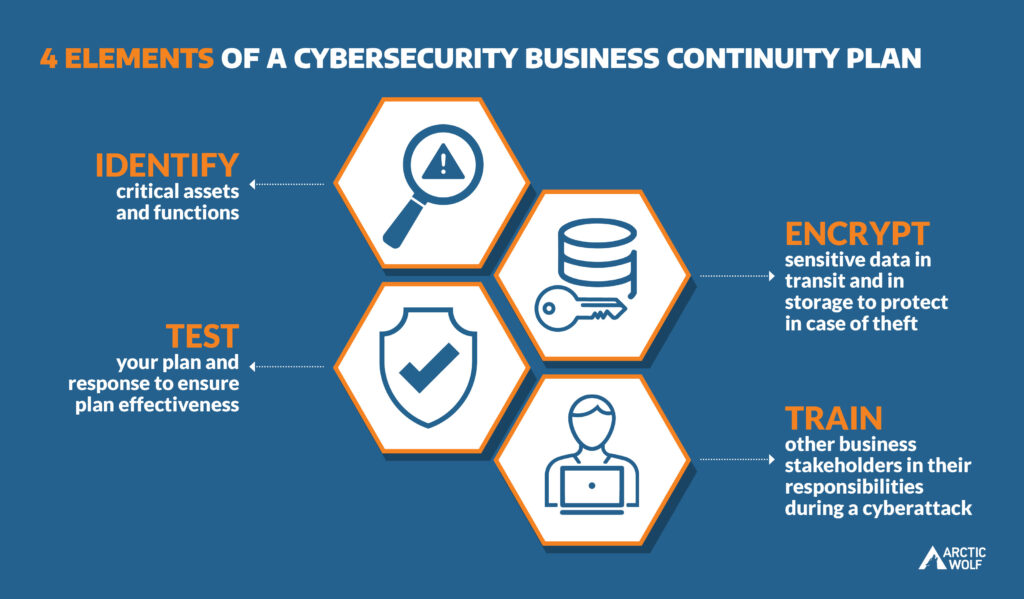
Recovery planning involves establishing protocols and strategies to restore systems and operations after a cybersecurity breach or failure. It includes identifying key assets, assessing risks, and developing comprehensive response plans. The primary goal is to ensure that, in the event of an attack—such as data breaches, ransomware, or other malicious activities—organizations can quickly recover and maintain business continuity.
The Importance of Recovery Planning
- Minimizing Downtime: Cyber incidents can lead to significant downtime, affecting productivity and revenue. A well-structured recovery plan helps organizations restore operations quickly, reducing the financial impact.
- Data Integrity and Protection: Recovery planning focuses on maintaining data integrity. Regular backups and secure restoration processes ensure that critical data remains intact and accessible, mitigating the risk of permanent loss.
- Regulatory Compliance: Many industries are subject to regulations that require organizations to have robust cybersecurity measures in place, including recovery plans. Compliance not only helps avoid legal penalties but also reinforces trust with clients and stakeholders.
- Reputation Management: In the wake of a cyber incident, public perception can significantly impact a business’s reputation. A swift and effective recovery demonstrates a commitment to security, fostering confidence among customers and partners.
Key Components of a Cybersecurity Recovery Plan
- Risk Assessment: Understand potential threats and vulnerabilities specific to your organization. This assessment should guide the development of tailored recovery strategies.
- Incident Response Team: Establish a dedicated team responsible for managing cyber incidents. This team should include members from IT, legal, and communications to ensure a holistic response.
- Communication Strategy: Develop a clear communication plan for internal and external stakeholders. Transparency during and after a cyber incident is crucial for maintaining trust and managing expectations.
- Backup Solutions: Implement regular backup protocols, ensuring data is stored securely off-site or in the cloud. Test restoration processes to confirm that backups can be accessed and restored efficiently.
- Training and Drills: Regular training for employees on cybersecurity best practices and conducting simulated recovery exercises helps ensure that everyone knows their roles and responsibilities during an incident.
- Continuous Improvement: Recovery planning is not a one-time task. Regularly review and update your recovery plan based on new threats, technological advancements, and lessons learned from past incidents.
Conclusion
In the face of evolving cyber threats, effective recovery planning is a vital component of a comprehensive cybersecurity strategy. By proactively preparing for potential incidents, organizations can minimize risks, protect vital assets, and ensure a swift return to normal operations. In doing so, they not only safeguard their data but also build a resilient framework that fosters trust and confidence among customers and stakeholders alike. Investing in recovery planning today will pay dividends in the event of a cyber crisis tomorrow.
You Might Also Like These: