Recovery Planning Cyber Security Nist, In an era where cyber threats loom larger than ever, organizations must prioritize robust recovery planning as a core component of their cybersecurity strategy. The National Institute of Standards and Technology (NIST) provides a comprehensive framework that can guide organizations in developing effective recovery plans to ensure resilience in the face of cyber incidents.
Understanding Recovery Planning
Recovery planning refers to the strategies and procedures that an organization implements to restore its IT systems and operations after a disruptive event, such as a cyberattack. This planning is critical for minimizing downtime, protecting sensitive data, and ensuring continuity of business operations. Effective recovery planning enables organizations to respond swiftly to incidents, reduce potential losses, and maintain stakeholder trust.
The NIST Cybersecurity Framework
NIST has developed several publications to help organizations enhance their cybersecurity posture, with Special Publication 800-53 and the Cybersecurity Framework being particularly influential. These resources provide guidelines for managing cybersecurity risks and emphasize the importance of recovery planning.
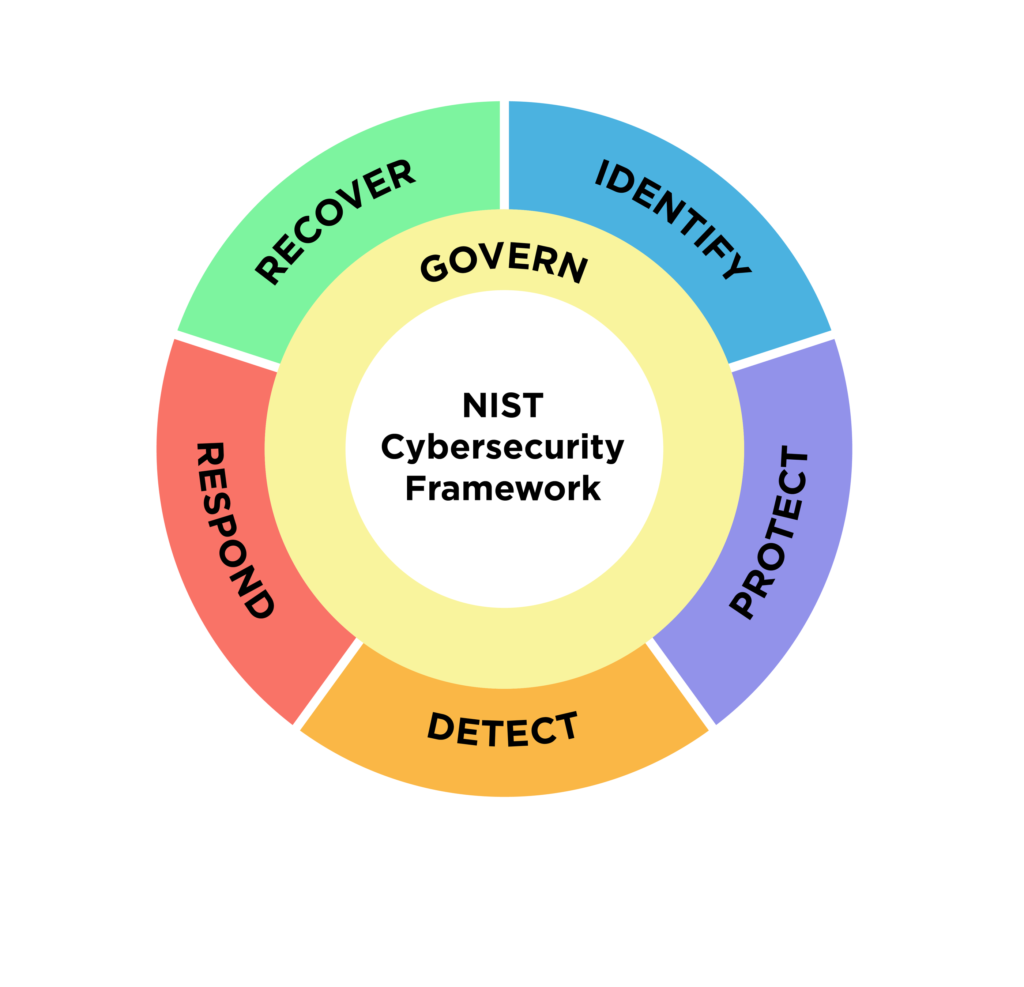
- Framework Core Functions: The NIST Cybersecurity Framework is structured around five core functions: Identify, Protect, Detect, Respond, and Recover. The “Recover” function is crucial, as it focuses on developing and implementing plans for resilience and restoration after a cybersecurity incident.
- Recovery Planning Guidelines: NIST Special Publication 800-34 offers specific guidance on contingency planning. This publication outlines the essential elements of a recovery plan, including:
- Planning and Preparation: Establishing a recovery team and defining roles and responsibilities.
- Risk Assessment: Identifying potential threats and vulnerabilities that could impact recovery efforts.
- Business Impact Analysis (BIA): Analyzing the potential impact of different types of disruptions on critical business functions.
- Recovery Strategies: Developing and documenting strategies for recovering IT systems, data, and applications, including backup solutions and alternative processing sites.
- Testing and Maintenance: Regularly testing the recovery plan to ensure its effectiveness and updating it as necessary to reflect changes in the organization or its environment.
Implementing NIST Guidelines for Effective Recovery Planning
To align recovery planning efforts with NIST guidelines, organizations should consider the following steps:
- Conduct a Comprehensive Risk Assessment: Understanding the specific risks your organization faces is the foundation of effective recovery planning. Regularly assess the threat landscape and adjust recovery strategies accordingly.
- Develop and Document Recovery Procedures: Clearly outline recovery procedures and ensure they are easily accessible. This documentation should include step-by-step instructions for restoring systems, data, and applications.
- Establish Communication Protocols: In the event of a cyber incident, effective communication is key. Develop protocols to inform stakeholders, including employees, customers, and partners, about the status of recovery efforts.
- Regularly Test the Recovery Plan: Conducting tabletop exercises and simulations can help identify gaps in the recovery plan. Use these tests to refine procedures and ensure that all team members are familiar with their roles.
- Continuous Improvement: Recovery planning is not a one-time effort. Continuously monitor and update the recovery plan based on lessons learned from tests, actual incidents, and changes in technology or business operations.
Conclusion
Recovery planning is an essential aspect of any cybersecurity strategy, especially in today’s threat landscape. By aligning recovery efforts with NIST guidelines, organizations can develop comprehensive plans that enhance resilience and ensure a swift return to normal operations following a cyber incident. The proactive approach of recovery planning not only minimizes disruption but also reinforces an organization’s commitment to protecting its assets and maintaining stakeholder confidence in the face of adversity.
You Might Also Like These:
cyber security disaster recovery plan template
cyber security disaster recovery plan template
cyber attack disaster recovery plan template
effective practices for cyber incident response and recovery