Cyber Recovery Dell, In today’s digital landscape, the threat of cyberattacks is more prevalent than ever. With ransomware and data breaches on the rise, organizations are increasingly prioritizing their cyber recovery strategies. Dell Technologies, a leader in IT solutions, offers robust cyber recovery solutions designed to help businesses safeguard their data and ensure business continuity in the event of a cyber incident. This article explores Dell’s cyber recovery offerings and how they can benefit organizations of all sizes.
Understanding Cyber Recovery
Cyber recovery refers to the processes and technologies used to restore data and systems after a cyberattack or data loss incident. It encompasses a range of strategies, including data backup, disaster recovery planning, and cybersecurity measures to prevent future incidents. A well-defined cyber recovery plan is essential for organizations to minimize downtime, protect sensitive information, and maintain customer trust.
Dell’s Cyber Recovery Solutions
Dell Technologies provides a comprehensive suite of cyber recovery solutions that integrate seamlessly into existing IT infrastructures. Here are some key components of Dell’s approach:
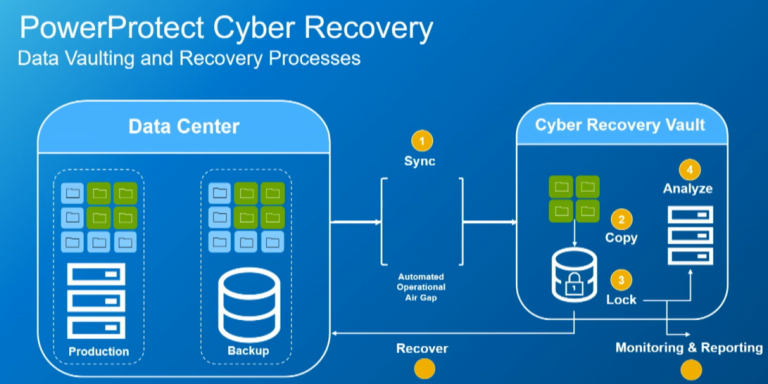
- Data Protection and Backup: Dell’s data protection solutions, such as Dell EMC Data Domain and PowerProtect, offer efficient and secure backup options. These solutions ensure that data is regularly backed up and can be quickly restored in the event of a cyberattack. They utilize advanced deduplication technology to reduce storage requirements and improve recovery times.
- Disaster Recovery Orchestration: Dell’s recovery solutions include orchestration tools that automate the disaster recovery process. These tools streamline the recovery of applications and systems, reducing the time and effort required to restore operations after an attack.
- Cyber Recovery Vault: One of the standout features of Dell’s cyber recovery offerings is the Cyber Recovery Vault. This isolated environment stores backup data securely and is designed to withstand cyberattacks. The vault protects critical data from ransomware and other malicious activities, ensuring that businesses can recover their data even in the most severe incidents.
- Comprehensive Security Features: Dell’s cyber recovery solutions come with built-in security features to protect against unauthorized access and data breaches. These include encryption, access controls, and regular security updates to safeguard sensitive information.
- Consulting and Support Services: Dell Technologies offers consulting services to help organizations assess their cyber recovery needs and develop tailored strategies. Their team of experts can provide guidance on best practices, compliance requirements, and incident response planning.
Benefits of Dell’s Cyber Recovery Solutions
- Rapid Recovery: Dell’s solutions are designed for fast recovery, minimizing downtime and enabling businesses to return to normal operations quickly.
- Cost-Effectiveness: By utilizing Dell’s advanced backup and recovery technologies, organizations can reduce the costs associated with data loss and downtime.
- Scalability: Dell’s cyber recovery solutions are scalable, allowing businesses to expand their recovery capabilities as their data grows.
- Enhanced Security: With features like the Cyber Recovery Vault and robust security measures, organizations can protect their data against evolving cyber threats.
Conclusion
In an era where cyber threats are an unfortunate reality, having a solid cyber recovery strategy is crucial for businesses. Dell Technologies offers comprehensive cyber recovery solutions that empower organizations to protect their data, ensure business continuity, and respond effectively to cyber incidents. By investing in Dell’s cyber recovery offerings, businesses can enhance their resilience against cyberattacks and safeguard their most valuable asset—data.
In summary, cyber recovery with Dell is not just about recovering data; it’s about building a stronger, more secure future for organizations navigating the complexities of the digital world.
You Might Also Like These: