Cyber Security Recovery Plan Sample, In today’s digital landscape, cyber threats are more prevalent than ever. Businesses of all sizes are at risk of cyberattacks, making it essential to have a robust Cyber Security Recovery Plan in place. A well-structured recovery plan not only helps organizations respond to incidents effectively but also ensures a swift return to normal operations. This article outlines the key components of a Cyber Security Recovery Plan and provides a sample framework that businesses can adapt to their specific needs.
Understanding the Importance of a Cyber Security Recovery Plan
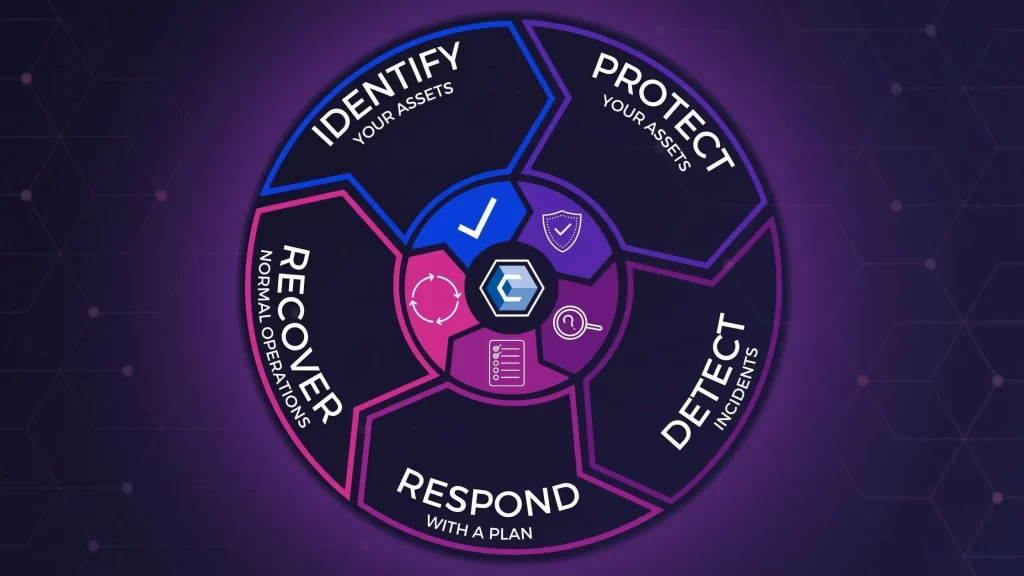
A Cyber Security Recovery Plan is a comprehensive strategy designed to help organizations recover from cyber incidents, such as data breaches, ransomware attacks, or system failures. The primary goals of such a plan include:
- Minimizing Downtime: Reducing the time it takes to restore systems and services after an incident.
- Protecting Data: Ensuring the integrity and confidentiality of sensitive information during and after a cyber incident.
- Maintaining Trust: Preserving customer confidence by demonstrating preparedness and resilience.
- Regulatory Compliance: Meeting legal and industry-specific requirements for data protection and incident response.
Key Components of a Cyber Security Recovery Plan
- Risk Assessment: Identify potential threats and vulnerabilities that could impact your organization. This includes assessing the likelihood and potential impact of various cyber threats.
- Incident Response Team: Establish a dedicated team responsible for managing incidents. This team should include representatives from IT, legal, compliance, and communications to ensure a coordinated response.
- Communication Plan: Develop a clear communication strategy for internal and external stakeholders. This plan should outline how information will be shared during and after an incident.
- Backup and Data Recovery: Implement regular data backups and establish a recovery process to restore data and systems quickly. Ensure that backups are stored securely and are tested regularly.
- Business Continuity Plan: Create a business continuity strategy that outlines how critical business functions will be maintained during a cyber incident. This may include alternative work arrangements, such as remote work or temporary relocation.
- Training and Awareness: Provide regular training for employees on cybersecurity best practices and incident response protocols. This helps create a culture of security within the organization.
- Review and Update: Regularly review and update the recovery plan to address new threats, changes in technology, and lessons learned from previous incidents.
Cyber Security Recovery Plan Sample Framework
Here’s a sample framework for a Cyber Security Recovery Plan that organizations can customize according to their specific needs:
1. Introduction
- Purpose of the plan
- Scope of the recovery efforts
2. Risk Assessment
- Overview of identified threats
- Vulnerability assessment results
3. Incident Response Team
- Roles and responsibilities
- Contact information for team members
4. Incident Response Procedures
- Initial detection and reporting
- Incident assessment and categorization
- Containment strategies
- Eradication of threats
- Recovery procedures
5. Backup and Data Recovery
- Backup schedule and locations
- Data recovery processes and responsibilities
6. Communication Plan
- Internal communication protocols
- External communication guidelines (customers, stakeholders, media)
7. Business Continuity Strategies
- List of critical business functions
- Recovery time objectives (RTO) and recovery point objectives (RPO)
8. Training and Awareness
- Training schedule for employees
- Resources for ongoing education
9. Plan Review and Maintenance
- Schedule for regular reviews and updates
- Process for documenting lessons learned
Conclusion
A Cyber Security Recovery Plan is essential for any organization seeking to protect itself from the ever-evolving landscape of cyber threats. By understanding the key components of such a plan and implementing a tailored framework, businesses can enhance their resilience against cyber incidents and ensure a swift recovery. Regular updates and training are critical to maintaining an effective recovery strategy, enabling organizations to thrive in the digital age.
You Might Also Like These: