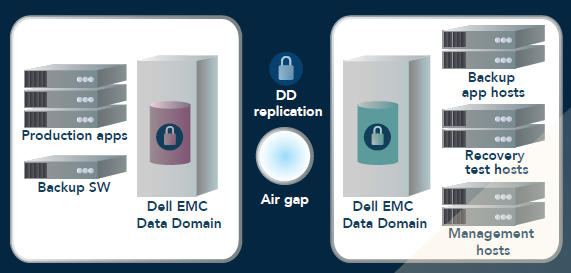
Cyber Recovery Solution, In today’s digital landscape, businesses are increasingly reliant on technology for their operations. This reliance, however, comes with a heightened risk of cyber threats. From ransomware attacks to data breaches, the stakes have never been higher. As a result, organizations must adopt a robust cyber recovery solution to safeguard their assets, maintain business continuity, and ensure rapid recovery in the event of a cyber incident.
What is a Cyber Recovery Solution?
A cyber recovery solution encompasses a suite of strategies, tools, and processes designed to protect an organization’s data and IT infrastructure from cyber threats. Its primary purpose is to ensure that businesses can recover swiftly and efficiently after an attack, minimizing downtime and data loss. These solutions typically involve:
- Data Backup: Regularly backing up critical data is a foundational aspect of any cyber recovery strategy. Backup solutions should be automated and stored in secure, offsite locations to protect against data loss caused by cyber incidents.
- Incident Response Planning: A well-defined incident response plan is crucial. This plan outlines the steps to take in the event of a cyberattack, including communication strategies, roles and responsibilities, and recovery procedures.
- Disaster Recovery Solutions: These involve specific technologies and services that allow businesses to restore their IT systems and data following an incident. This could include cloud-based recovery services, which provide flexibility and scalability.
- Regular Testing and Drills: Testing the effectiveness of a cyber recovery solution is essential. Organizations should conduct regular drills to simulate cyber incidents and evaluate the response plan’s effectiveness.
- Employee Training: Human error is often a significant factor in cyber incidents. Therefore, training employees on cybersecurity best practices is vital. This includes recognizing phishing attempts, safe browsing habits, and proper data handling.
Benefits of Implementing a Cyber Recovery Solution
Investing in a cyber recovery solution offers numerous benefits:
- Minimized Downtime: Quick recovery capabilities help businesses resume operations swiftly, reducing the financial impact of downtime.
- Data Integrity and Security: Regular backups and robust security measures help maintain the integrity and security of sensitive data.
- Regulatory Compliance: Many industries have strict data protection regulations. A comprehensive cyber recovery solution helps organizations comply with these requirements.
- Enhanced Customer Trust: Demonstrating a commitment to cybersecurity can enhance customer trust and confidence in the organization.
Choosing the Right Cyber Recovery Solution
Selecting the right cyber recovery solution requires careful consideration of various factors:
- Business Needs: Assess the specific needs of your organization, including the types of data that need protection and the potential impact of downtime.
- Scalability: As businesses grow, their cyber recovery solutions should be able to scale accordingly. Look for solutions that can adapt to changing needs.
- Expertise and Support: Consider whether your organization has the necessary in-house expertise to manage the solution or if you need to partner with a third-party provider for support.
Conclusion
In an era where cyber threats are pervasive and increasingly sophisticated, a cyber recovery solution is not just a luxury; it is a necessity. By implementing a robust recovery strategy, businesses can protect themselves from the devastating effects of cyber incidents, ensuring resilience and continuity in their operations. Investing in such solutions not only safeguards data but also enhances overall trust in the organization, paving the way for sustainable growth in the digital age.
You Might Also Like These:
cyber attack disaster recovery template
disaster recovery plan cyber security example