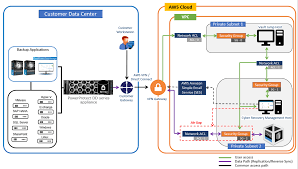
Understanding Cyber Recovery Tokens: The Next Frontier in Data Protection
Cyber Recovery Tokens, In today’s rapidly evolving digital landscape, organizations face an array of cybersecurity threats that continually grow in both volume and sophistication. Cyberattacks can not only disrupt business operations but also compromise sensitive data and lead to substantial financial and reputational losses. One emerging approach to enhancing data security and resilience against cyberattacks …
Understanding Cyber Recovery Tokens: The Next Frontier in Data Protection Read More »