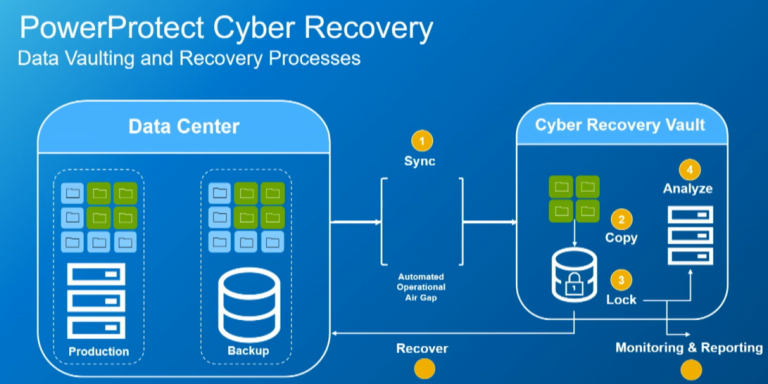
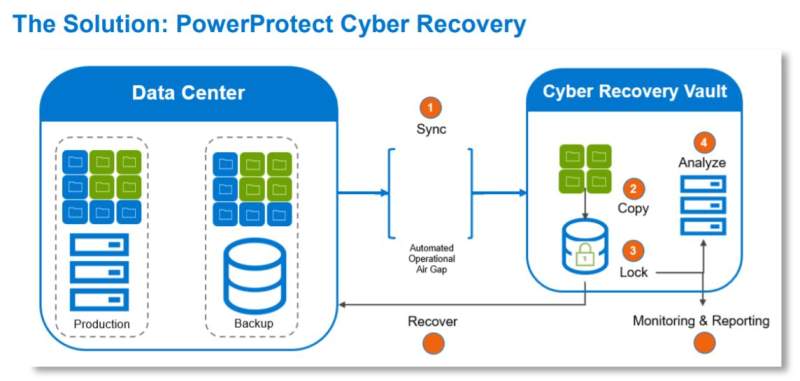
Recovery Plan After a Cyber Attack: Essential Steps for Businesses
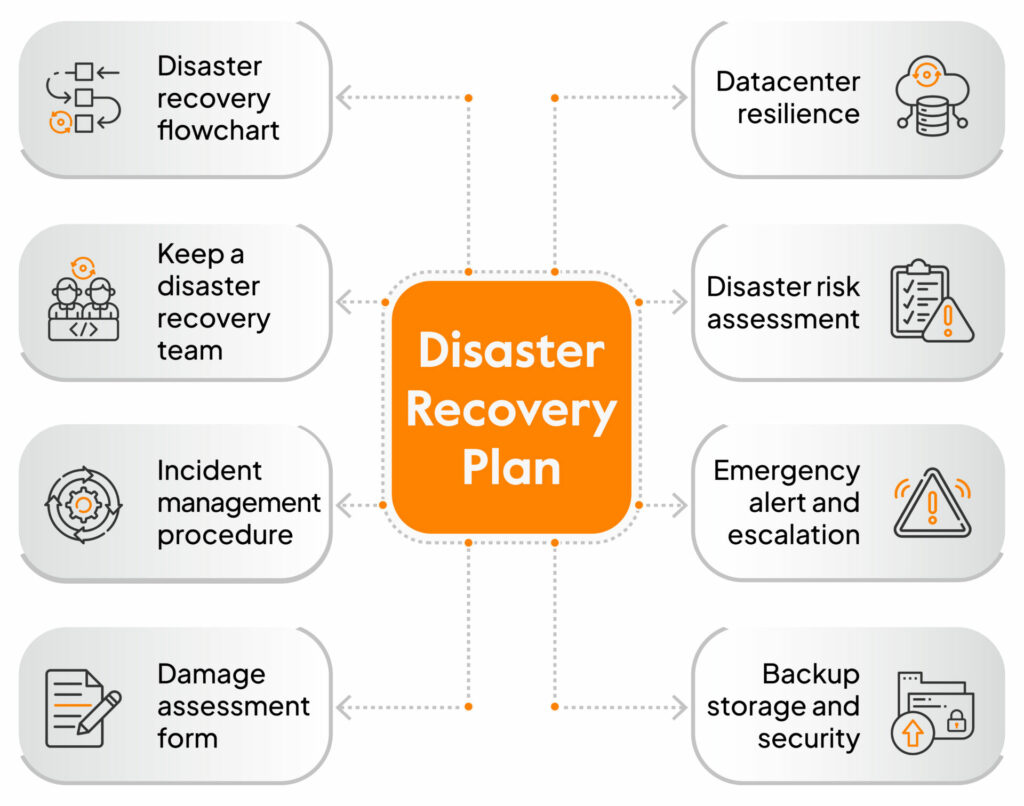
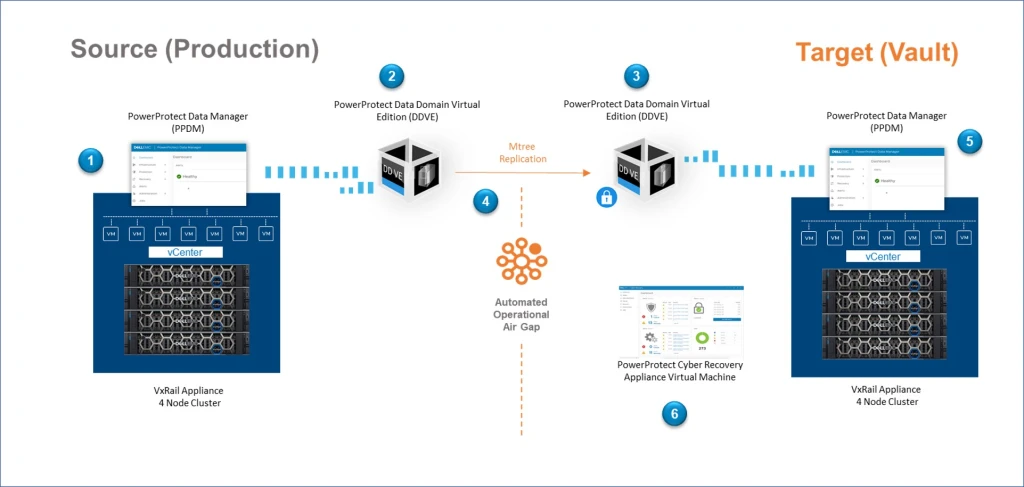
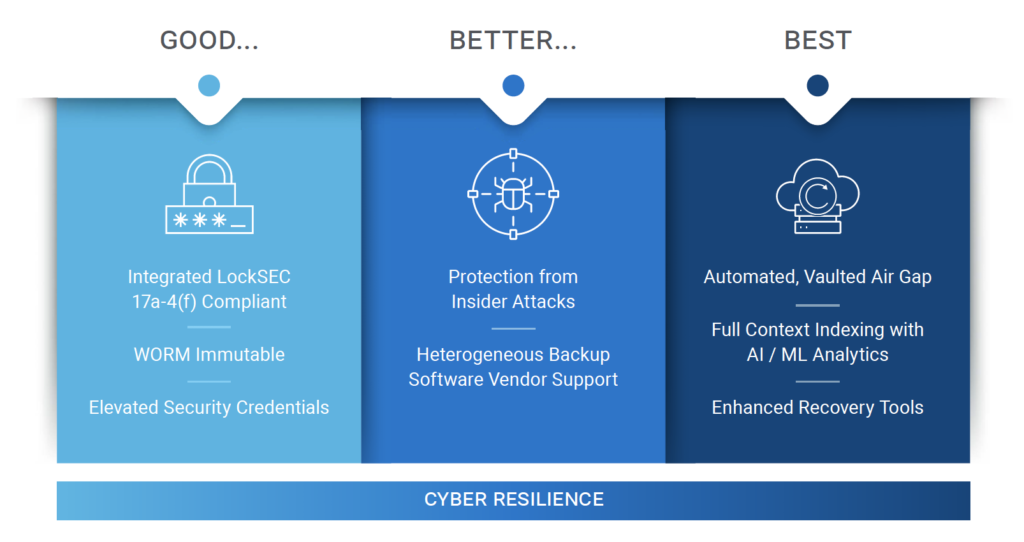
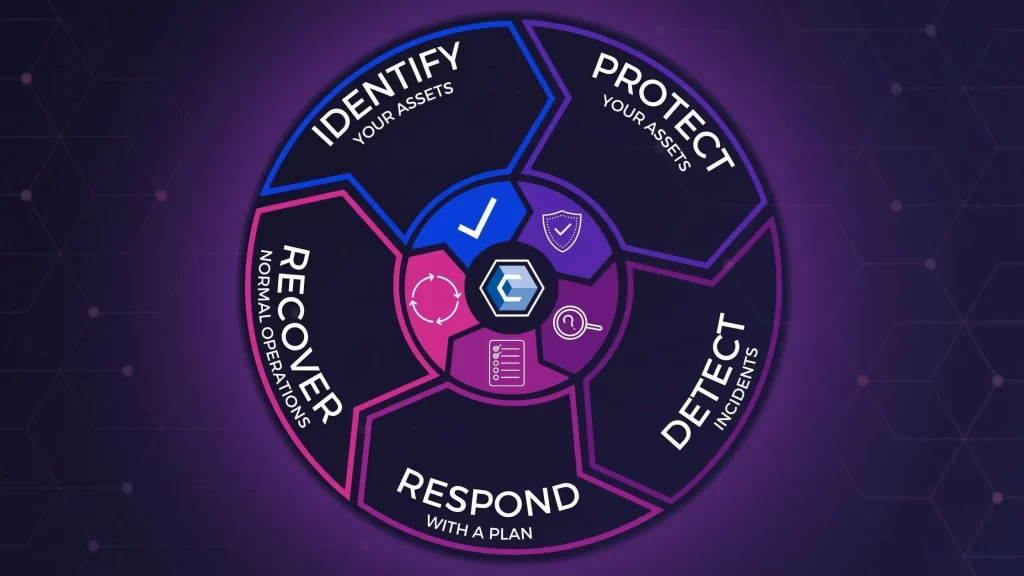
Recovery Plan After Cyber Attack, In today’s interconnected world, the risk of cyber attacks has escalated, making it crucial for businesses to have a robust recovery plan in place. A well-structured recovery plan after a cyber attack not only mitigates damage but also ensures a swift return to normal operations. Here’s a comprehensive guide to …
Recovery Plan After a Cyber Attack: Essential Steps for Businesses Read More »