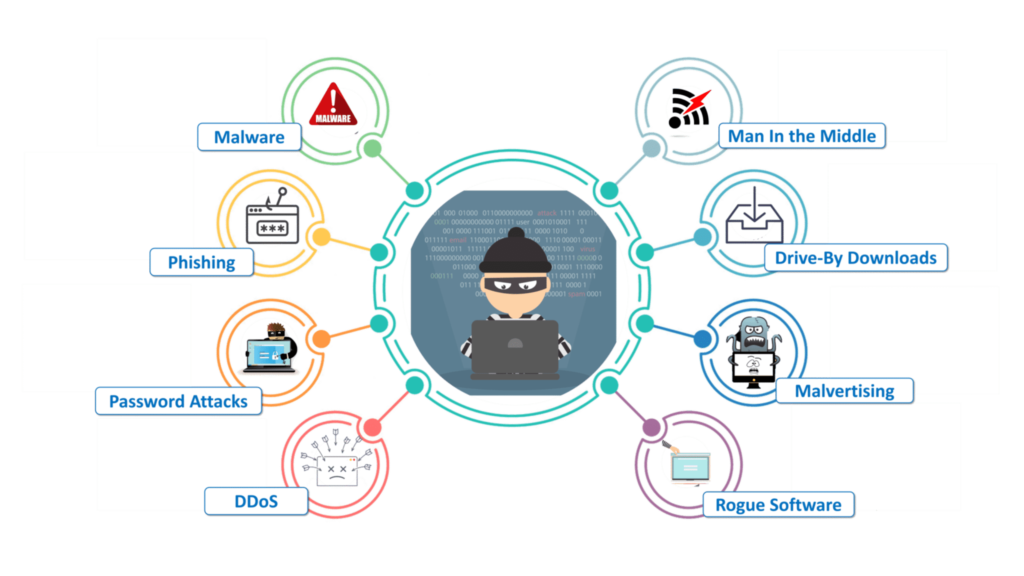
Chapter 5 Quiz Recovery Cyber Security, In the ever-evolving field of cyber security, understanding the nuances of quiz recovery methods is essential for both professionals and students. Chapter 5 of many cyber security textbooks often delves into various recovery techniques and strategies that can be employed to safeguard sensitive information and ensure continuity in the face of potential data breaches or cyber attacks. This article will explore the key concepts presented in Chapter 5 regarding quiz recovery and how they can be applied in real-world scenarios.
The Importance of Data Recovery
Data recovery refers to the process of restoring lost, deleted, or inaccessible data from storage devices. In the context of cyber security, this is particularly critical as organizations strive to maintain their integrity and confidentiality amidst increasing cyber threats. A robust quiz recovery plan not only protects sensitive data but also contributes to an organization’s overall risk management strategy.
Key Concepts in Quiz Recovery
- Understanding Vulnerabilities: Chapter 5 typically begins by outlining common vulnerabilities that lead to data loss, such as hardware failures, accidental deletions, and cyber attacks. Recognizing these risks is the first step in formulating an effective recovery strategy.
- Data Backup Solutions: Effective quiz recovery often relies on regular data backups. Various methods exist, including full, incremental, and differential backups. Understanding the differences between these types of backups is crucial for selecting the most appropriate solution for an organization’s needs.
- Incident Response Planning: An incident response plan is an essential component of quiz recovery. It outlines the steps an organization must take in the event of a cyber incident. This plan should be regularly reviewed and updated to adapt to new threats and vulnerabilities.
- Testing Recovery Procedures: Regularly testing recovery procedures is vital to ensure they work effectively when needed. Simulations and drills can help identify weaknesses in the recovery process, allowing organizations to refine their strategies.
- Legal and Compliance Considerations: Organizations must be aware of legal and regulatory requirements surrounding data recovery. Compliance with laws such as GDPR or HIPAA is critical, as failure to comply can lead to significant penalties.
Real-World Applications
In practice, the concepts covered in Chapter 5 can be applied across various industries. For example, in healthcare, effective quiz recovery strategies can protect patient records and ensure compliance with HIPAA regulations. In finance, safeguarding sensitive customer data is paramount, and implementing robust recovery processes can help maintain trust and integrity.
Conclusion
Chapter 5 of cyber security textbooks provides essential insights into quiz recovery strategies that are vital for protecting an organization’s data. By understanding vulnerabilities, implementing regular backups, developing incident response plans, testing recovery procedures, and adhering to legal requirements, organizations can enhance their resilience against cyber threats. As the cyber landscape continues to change, staying informed and prepared is key to effective data recovery and overall cyber security.
You Might Also Like These:
cyber security disaster recovery plan template