Cyber Attack Scenario Disaster Recovery Plan, In today’s digital landscape, organizations are increasingly reliant on technology for their operations. This dependence, however, makes them vulnerable to cyber attacks that can disrupt business continuity and cause significant financial and reputational damage. Developing a robust cyber attack scenario disaster recovery plan is essential for mitigating risks and ensuring a swift response to potential cyber incidents.
Understanding Cyber Attack Scenarios
Cyber attack scenarios can vary widely, ranging from data breaches and ransomware attacks to distributed denial-of-service (DDoS) attacks and insider threats. Each scenario presents unique challenges and potential impacts on an organization. To effectively prepare for these threats, it is crucial to identify and analyze various attack vectors that could compromise sensitive data and systems.
Common Cyber Attack Scenarios
- Ransomware Attacks: Malicious software that encrypts data, demanding payment for decryption. This type of attack can halt operations and lead to data loss.
- Data Breaches: Unauthorized access to confidential data, often resulting in significant legal and financial consequences.
- DDoS Attacks: Overwhelming a network or website with traffic, rendering it inaccessible. These attacks can disrupt services and tarnish reputations.
- Phishing Attacks: Deceptive emails or messages designed to trick employees into divulging sensitive information, often leading to unauthorized access.
- Insider Threats: Employees or contractors who misuse their access to systems and data, intentionally or unintentionally causing harm.
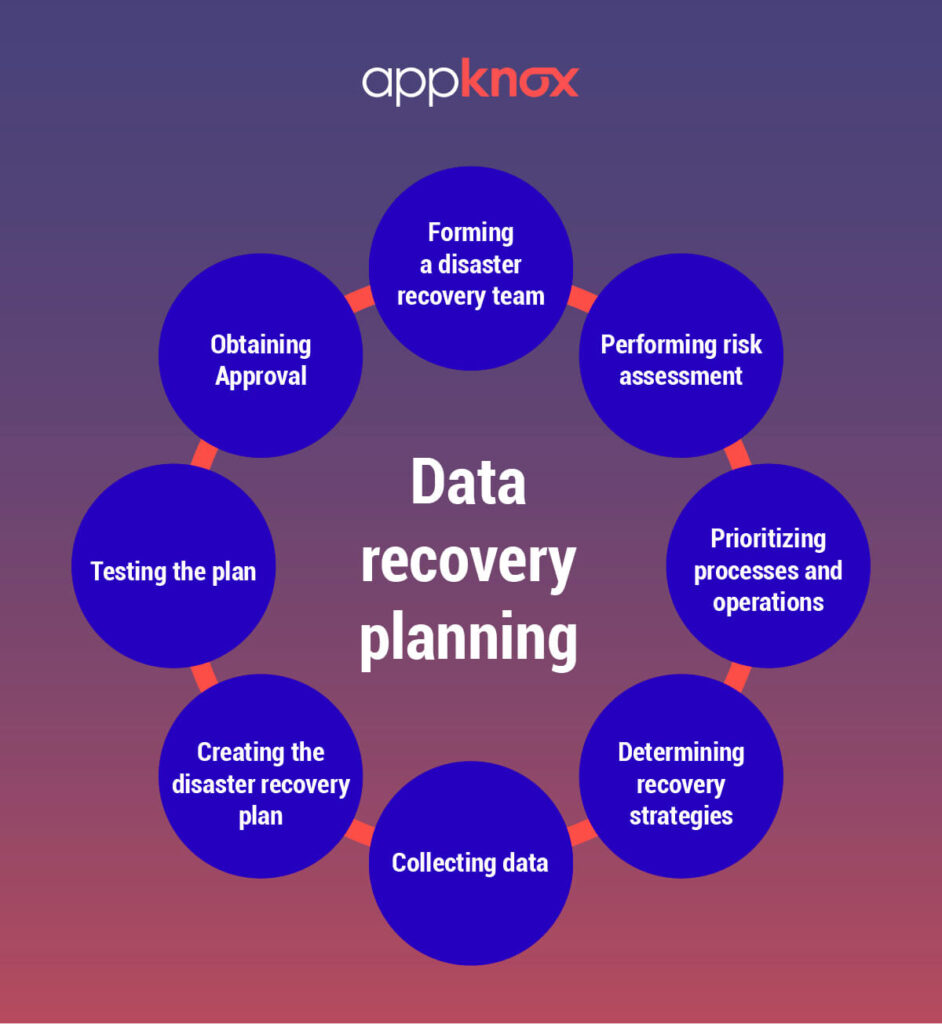
Developing a Disaster Recovery Plan
Creating a cyber attack scenario disaster recovery plan involves several key steps:
1. Risk Assessment
Begin by conducting a thorough risk assessment to identify vulnerabilities within your organization’s systems and processes. This includes evaluating your current cybersecurity measures, understanding potential threats, and assessing the potential impact of different cyber attack scenarios.
2. Establish Recovery Objectives
Define your recovery time objectives (RTO) and recovery point objectives (RPO). The RTO indicates how quickly you need to restore operations after an attack, while the RPO defines the maximum acceptable data loss in terms of time.
3. Develop Response Strategies
Create specific response strategies for each identified cyber attack scenario. This includes outlining immediate actions to contain the attack, such as isolating affected systems, notifying relevant stakeholders, and involving cybersecurity experts.
4. Create Communication Plans
Establish clear communication protocols to inform employees, customers, and stakeholders about the incident. Transparency is crucial for maintaining trust and managing reputational risks during a cyber attack.
5. Implement Backup Solutions
Regularly back up critical data and systems to ensure data integrity. Consider using off-site or cloud-based backups to protect against ransomware and other destructive attacks.
6. Conduct Training and Simulations
Regularly train employees on recognizing and responding to cyber threats. Conduct simulation exercises to test your disaster recovery plan, allowing your team to practice their responses in a controlled environment.
7. Review and Update the Plan
Cyber threats are constantly evolving, making it essential to regularly review and update your disaster recovery plan. This ensures that your organization remains prepared for emerging threats and maintains a robust security posture.
Conclusion
A well-developed cyber attack scenario disaster recovery plan is an essential component of an organization’s overall cybersecurity strategy. By proactively identifying potential threats, establishing clear response strategies, and regularly training employees, organizations can minimize the impact of cyber attacks and ensure a swift recovery. In a world where cyber threats are ever-present, preparation is the key to resilience.
You Might Also Like These:
cyber recovery solution dell emc
ransomware disaster recovery plan template
cyber security disaster recovery plan example