Cyber Incident Management + Recovery Plan, In today’s digitally driven world, organizations are increasingly vulnerable to cyber threats. From phishing attacks to sophisticated ransomware campaigns, cyber incidents can cripple business operations, cause significant financial loss, and damage reputations. Having a cyber incident management and recovery plan is no longer optional—it is a critical necessity to ensure resilience and quick recovery when a security breach occurs.
Understanding Cyber Incident Management
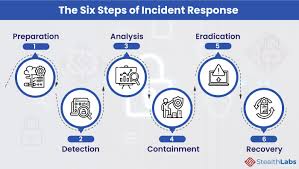
Cyber incident management refers to the process organizations follow to identify, manage, and respond to cybersecurity incidents. The goal is to contain and mitigate the impact of the incident as quickly as possible, restoring normal operations while minimizing harm.
A well-defined cyber incident management framework typically includes:
- Detection and Identification: Recognizing the signs of a cyberattack or data breach.
- Containment: Limiting the spread and impact of the threat to prevent further damage.
- Eradication: Removing the source of the attack from the network.
- Recovery: Restoring affected systems and services to full operational capacity.
- Post-Incident Review: Analyzing the incident to understand what went wrong and how future attacks can be prevented.
The Role of a Recovery Plan in Cyber Incident Management
A recovery plan is a comprehensive guide that details the steps an organization must take to recover from a cyber incident. While the incident management process focuses on addressing the immediate threat, the recovery plan ensures that long-term damage is minimized and that normal business operations are restored efficiently.
A successful cyber recovery plan includes:
- System Backups: Regular backups of critical data to ensure availability in case of data loss.
- Communication Protocols: Predefined channels for communicating with employees, stakeholders, and possibly the public.
- Data Restoration Procedures: Clear steps to restore data, including prioritization of essential functions.
- Third-Party Vendor Management: Coordination with external vendors and service providers who can assist in the recovery process.
- Testing and Drills: Regular testing of the recovery plan to ensure preparedness and to identify weaknesses.
Why an Integrated Approach is Key
Organizations need to adopt an integrated approach that links their cyber incident management and recovery plans into a cohesive framework. Here’s why:
- Minimized Downtime: When incident management and recovery are coordinated, organizations can respond swiftly to breaches, minimizing system downtime and disruption.
- Improved Communication: A unified strategy ensures clear communication across teams, from technical staff managing the breach to executives making key decisions and public relations managing external communication.
- Reduced Financial Impact: The longer a breach remains active, the greater the financial and reputational damage. Effective incident management combined with a rapid recovery process reduces these risks.
- Compliance and Regulatory Requirements: Many industries are subject to strict regulations regarding data protection and breach notification. Having an integrated incident management and recovery plan ensures compliance with these laws, avoiding hefty fines and legal penalties.
Key Components of a Cyber Incident Management and Recovery Plan
A successful plan is detailed, strategic, and regularly updated. Key components include:
- Incident Response Team: A dedicated team of cybersecurity professionals who are trained to handle different types of cyber incidents.
- Forensic Analysis: The ability to investigate and understand the nature of the attack to improve future defenses.
- Business Continuity Planning: Ensuring critical business operations continue while recovery efforts are underway.
- Regular Training: Employees should be trained to recognize cybersecurity threats and respond appropriately in the event of an incident.
- Cybersecurity Insurance: Depending on the scale of the organization, cyber insurance may be part of the recovery plan, helping to cover costs associated with data breaches.
Final Thoughts: Future-Proofing with Incident Management and Recovery
Cyber threats are continually evolving, which means that cyber incident management and recovery plans must be dynamic. Regular updates, testing, and refinement are crucial to ensuring the effectiveness of these plans. By adopting a proactive, integrated approach, organizations can not only mitigate the impact of cyber incidents but also ensure a swift recovery, safeguarding both their reputation and bottom line.
In an era where cyberattacks are increasingly sophisticated, organizations cannot afford to be complacent. Preparedness is the key to resilience, and a robust incident management and recovery plan is the backbone of that preparedness.
You Might Also Like These:
cyber attack disaster recovery template