Cyber Incident Management + Recovery Planning, In today’s digital landscape, organizations face an ever-increasing number of cyber threats that can disrupt operations, compromise data, and harm reputations. To combat these risks, effective cyber incident management and recovery planning are crucial. This article explores the importance of these strategies and outlines key steps organizations can take to prepare for and respond to cyber incidents.
Understanding Cyber Incident Management
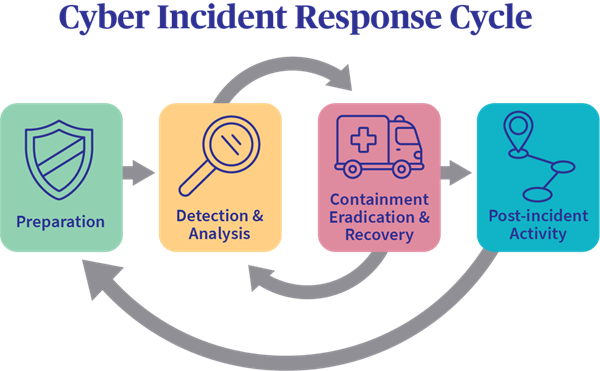
Cyber incident management involves a structured approach to identifying, managing, and mitigating the impact of cyber incidents. The primary goal is to minimize damage and restore normal operations as quickly as possible. A well-defined incident management process typically includes the following stages:
- Preparation: Organizations should establish policies, procedures, and response teams to address potential cyber threats. This phase includes training employees, conducting drills, and ensuring that tools and resources are in place.
- Detection and Analysis: Continuous monitoring and detection tools help identify potential incidents. Once detected, the incident must be analyzed to determine its scope and severity.
- Containment: Immediate steps should be taken to contain the incident and prevent further damage. This may involve isolating affected systems, revoking access rights, or implementing temporary network configurations.
- Eradication: After containment, the root cause of the incident must be identified and eliminated. This process may involve removing malware, patching vulnerabilities, or reconfiguring systems.
- Recovery: Organizations must restore systems to normal operations, ensuring that all affected data is recovered and that systems are secure before going back online.
- Post-Incident Review: After resolving the incident, conducting a thorough review is essential. This review should assess the response process, identify lessons learned, and suggest improvements for future incident management.
The Importance of Recovery Planning
Recovery planning is a vital aspect of cyber incident management. It ensures that organizations can quickly return to normal operations after an incident. An effective recovery plan addresses both technical and operational aspects and should include:
- Business Impact Analysis (BIA): Organizations should conduct a BIA to understand the potential impact of various incidents on their operations. This analysis helps prioritize recovery efforts based on critical business functions.
- Recovery Strategies: Develop strategies for recovering data and systems based on the results of the BIA. This may include offsite backups, cloud-based solutions, or alternate operational facilities.
- Communication Plan: Establish a clear communication strategy to inform stakeholders, employees, and customers about the incident and recovery efforts. Effective communication can help maintain trust and manage reputational risks.
- Testing and Maintenance: Regularly test recovery plans through simulations and tabletop exercises to ensure they are effective and up-to-date. Maintain documentation and review plans periodically to adapt to changes in the organization or threat landscape.
- Compliance Considerations: Be aware of relevant regulations and standards that may impact recovery planning, such as GDPR, HIPAA, or NIST guidelines. Ensure that recovery plans meet these requirements to avoid legal and financial penalties.
Conclusion
As cyber threats continue to evolve, organizations must prioritize cyber incident management and recovery planning to safeguard their operations. By developing a structured approach to incident management and establishing robust recovery strategies, organizations can enhance their resilience against cyber incidents. Proactive planning, continuous improvement, and effective communication are key to navigating the complexities of the digital landscape and ensuring long-term success in the face of cyber challenges.
You Might Also Like These:
disaster recovery in cyber security