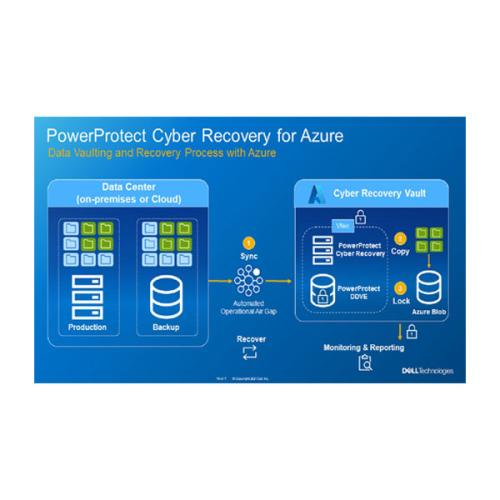
Cyber Power Recovery, In an era increasingly dominated by technology, the importance of maintaining uninterrupted access to digital resources cannot be overstated. The term “cyber power recovery” refers to the strategies and practices that organizations implement to restore and safeguard their digital infrastructure following a cyber incident or disruption. As cyber threats evolve and become more sophisticated, effective recovery measures have become essential for both businesses and individuals alike.
Understanding Cyber Power Recovery
Cyber power recovery encompasses a broad spectrum of actions aimed at restoring systems and data after a cyber event, such as a ransomware attack, data breach, or natural disaster. This process includes not only restoring functionality but also ensuring that data integrity is maintained and that systems are fortified against future threats. The ultimate goal is to minimize downtime and mitigate the impact of disruptions on operations and reputation.
Key Components of Cyber Power Recovery
- Risk Assessment and Planning: The first step in any recovery strategy is conducting a comprehensive risk assessment. Organizations must identify potential vulnerabilities in their systems and develop a robust incident response plan. This plan should detail the steps to take during an incident, the roles of team members, and the communication protocols to follow.
- Data Backup Solutions: Effective data backup is crucial for cyber power recovery. Regularly scheduled backups, both on-site and off-site, ensure that critical information can be restored quickly. The 3-2-1 backup rule—keeping three copies of data, on two different media, with one copy off-site—provides a solid framework for organizations to follow.
- Incident Response Team: Having a dedicated incident response team is vital for managing cyber incidents. This team should be trained to act swiftly and efficiently, containing the incident, mitigating damage, and beginning the recovery process. Their expertise can significantly reduce the time it takes to return to normal operations.
- Testing and Drills: Regularly testing recovery plans through simulations and drills ensures that staff are prepared for real incidents. These exercises can help identify gaps in the recovery strategy and provide opportunities for training and improvement.
- Continuous Monitoring and Improvement: Cyber threats are constantly evolving, making it essential for organizations to continuously monitor their systems and update their recovery plans. This proactive approach allows organizations to adapt to new threats and vulnerabilities.
The Role of Technology in Recovery
Advancements in technology play a crucial role in enhancing cyber power recovery efforts. Solutions such as cloud computing, artificial intelligence, and machine learning can improve data recovery times and optimize incident response. For instance, cloud-based backup solutions offer scalability and flexibility, allowing organizations to recover quickly from a variety of incidents without the need for extensive on-premises infrastructure.
Additionally, automated recovery tools can streamline the restoration process, reducing the risk of human error and expediting the return to operational status. Organizations should consider investing in advanced cybersecurity technologies that provide real-time threat detection and response capabilities, which are essential for minimizing damage during a cyber incident.
Conclusion
In today’s digital landscape, cyber power recovery is not just an IT concern; it is a critical business function that can determine the longevity and resilience of an organization. By implementing robust recovery strategies, investing in technology, and fostering a culture of preparedness, businesses can significantly enhance their ability to withstand and recover from cyber threats. As we continue to navigate the complexities of the digital age, prioritizing cyber power recovery will be essential for sustaining growth and ensuring security in an ever-evolving threat environment.
You Might Also Like These: