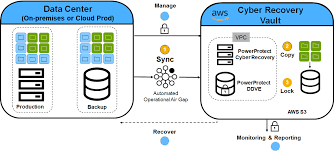
Cyber Recovery Services, In today’s rapidly evolving digital landscape, businesses rely more than ever on their data and IT infrastructure to function smoothly. However, with this increased dependency comes the heightened risk of cyberattacks, data breaches, and system failures. As cyber threats grow more sophisticated, businesses need robust strategies to ensure their continuity and resilience. This is where Cyber Recovery Services come into play, offering organizations a safety net in the face of cyber incidents.
What Are Cyber Recovery Services?
Cyber Recovery Services encompass a set of specialized strategies, technologies, and processes designed to restore critical business operations after a cyberattack or major system failure. These services go beyond traditional backup and disaster recovery by focusing specifically on recovering from security breaches, ransomware attacks, or other malicious activities that compromise data integrity.
Rather than merely restoring data from backups, Cyber Recovery Services emphasize isolating, diagnosing, and fixing the source of the breach while ensuring that the recovery process is secure, compliant, and efficient.
Why Are Cyber Recovery Services Essential?
- Rising Threat of Cyberattacks: In recent years, the frequency and complexity of cyberattacks have skyrocketed. From ransomware to advanced persistent threats (APTs), businesses face attacks that can cripple operations, resulting in massive financial losses and reputational damage. Cyber Recovery Services provide a systematic approach to mitigating these risks, helping businesses recover quickly and reduce downtime.
- Data Integrity and Compliance: In the event of a cyberattack, it’s not enough to simply retrieve lost data. Businesses need to ensure that the data is uncorrupted, safe from future threats, and in compliance with industry regulations. Cyber Recovery Services offer the necessary expertise to validate and safeguard recovered data, ensuring compliance with standards like GDPR, HIPAA, and others.
- Minimizing Downtime: Cyber incidents can disrupt operations, often leading to extended downtime. For businesses, time is money. Cyber Recovery Services prioritize business continuity by enabling swift recovery processes, ensuring that core functions return to normal as quickly as possible.
- Comprehensive Protection: While traditional disaster recovery solutions focus on hardware or system failures, Cyber Recovery Services provide a more holistic approach, incorporating defense mechanisms against human-made disasters like hacking and insider threats. This comprehensive protection helps companies face an ever-expanding threat landscape.
Key Components of Cyber Recovery Services
- Isolated Recovery Environments (IREs): IREs create secure, isolated environments where data can be stored, analyzed, and recovered without the risk of being contaminated by ongoing cyberattacks. These isolated environments prevent attackers from accessing recovery points, making it harder for them to re-infiltrate systems.
- Data Vaulting: Data vaulting ensures that critical business data is protected in secure, offsite storage, physically or logically separated from the rest of the IT infrastructure. This process helps ensure that even if a cyberattack breaches the main network, the company’s essential data remains safe and recoverable.
- Real-Time Threat Monitoring and Analytics: Advanced analytics tools are used to detect and analyze cyber threats in real time, providing valuable insights into the nature of the attack and how to mitigate it. Cyber Recovery Services often include forensic analysis, helping businesses understand how the attack occurred and how to prevent future incidents.
- Automated and Manual Recovery Processes: Automation is critical in ensuring quick recovery from cyber incidents. Automated processes streamline data restoration and verification, but manual intervention is often necessary to address complex issues and ensure proper oversight. A combination of both ensures that the recovery process is efficient and thorough.
- Post-Recovery Remediation: Once data is recovered, Cyber Recovery Services also include post-recovery measures such as patching vulnerabilities, reinforcing security protocols, and providing recommendations to prevent future attacks. This phase is crucial for reducing the chances of a repeat incident.
Benefits of Cyber Recovery Services
- Faster Response to Cyber Incidents: Immediate response capabilities enable businesses to recover quickly and minimize damage after a cyberattack, preventing extended downtime and financial losses.
- Enhanced Business Continuity: By having a structured cyber recovery plan in place, businesses can ensure ongoing operations even in the face of severe disruptions, providing peace of mind for stakeholders.
- Protection Against Repeated Attacks: By isolating threats and providing a comprehensive recovery plan, Cyber Recovery Services help businesses safeguard their systems against similar attacks in the future.
- Cost Savings: A well-executed cyber recovery strategy reduces the long-term costs of recovering from an attack, especially when considering the potential losses from data breaches, legal actions, and lost business.
- Increased Customer Trust: By demonstrating resilience and preparedness, businesses can enhance their reputation with clients and partners, assuring them that sensitive data is well-protected.
Conclusion
Cyber threats are no longer a matter of “if” but “when” for many organizations. Cyber Recovery Services play a critical role in helping businesses prepare for, respond to, and recover from these inevitable threats. By incorporating robust recovery solutions that focus specifically on cyber incidents, companies can ensure operational resilience, protect their critical assets, and maintain trust with customers and stakeholders. In an increasingly digital world, Cyber Recovery Services are not just an option but a necessity for businesses that want to thrive amidst growing cyber risks.
You Might Also Like These:
Understanding CWM Forex Fraud: A Cautionary Tale for Traders
Understanding Forex Broker Frauds: Protecting Yourself in the Trading World
How to Avoid Forex Fraud: Essential Tips for Traders
Forex Fraud Recovery: Steps to Recover Your Lost Funds
Understanding Chargeback Forex Fraud: A Guide to Protecting Yourself