Cyber Recovery Vault Delimc, In the rapidly evolving landscape of cybersecurity, businesses are constantly on the lookout for solutions to safeguard their most valuable asset: data. One of the most promising innovations in this field is the cyber recovery vault, specifically developed by Dell EMC (commonly referred to as DELL EMC Cyber Recovery Vault). This specialized approach to data protection offers an isolated, secure environment to shield critical business data from ransomware attacks and other cyber threats.
What is a Cyber Recovery Vault?
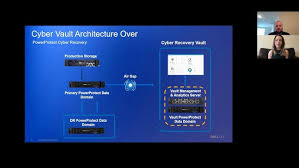
A cyber recovery vault is a highly secure, isolated data storage solution designed to protect data from cyberattacks by disconnecting it from the main network. The vault operates by creating air-gapped, immutable copies of data in a separate, offline environment. This means that even if hackers compromise a business’s primary network, the data within the cyber recovery vault remains untouched and inaccessible, ensuring businesses have a clean backup to recover from.
Dell EMC, a leader in IT infrastructure, introduced the Cyber Recovery Vault as a powerful tool in this space. Built to complement broader cybersecurity strategies, this solution offers businesses a critical layer of defense against sophisticated threats like ransomware, which often targets backup systems after breaching the network.
Key Features of the Dell EMC Cyber Recovery Vault
- Air-Gapped Isolation: The vault ensures that the critical data is stored offline and disconnected from the main business network. This isolation limits exposure to cyber threats, ensuring that attackers cannot access the data in real-time.
- Immutable Copies: Dell EMC’s Cyber Recovery Vault makes use of immutable storage, which creates unchangeable backup copies. Once a backup is written to the vault, it cannot be altered or deleted by malware, attackers, or even insider threats.
- Automated Data Synchronization and Validation: The vault regularly syncs with the primary network, but only in a controlled and secure manner. Additionally, the solution validates the integrity of the data, ensuring that no malicious code has slipped into the system before being saved in the vault.
- Data Analytics for Anomaly Detection: Leveraging advanced data analytics, Dell EMC’s vault actively monitors data for irregularities. If any unusual patterns are detected, the vault can flag them for further investigation, offering another layer of protection.
- Automated Recovery: In the event of an attack, businesses can quickly recover their data from the vault. Dell EMC’s solution is designed to minimize downtime, allowing companies to restore their systems efficiently and securely.
Why Businesses Need Cyber Recovery Vaults
Ransomware attacks are one of the biggest threats facing organizations today. Once a system is infected, attackers can hold data hostage until a ransom is paid, which often amounts to significant financial and reputational damage. Moreover, cybercriminals are increasingly targeting backup systems to ensure that businesses have no way to recover from the attack without paying up.
The Dell EMC Cyber Recovery Vault provides a critical defense against such scenarios. By storing data in an isolated and secure environment, businesses have a reliable fallback option that is out of reach of attackers.
In addition to ransomware, data breaches caused by insider threats or misconfigurations can also be mitigated using a cyber recovery vault. The immutable backups ensure that even if the main systems are compromised, the critical data remains untouched, and recovery is always possible.
Dell EMC Cyber Recovery Vault: The Future of Cybersecurity
With the growing sophistication of cyberattacks, traditional cybersecurity solutions like firewalls and antivirus software are no longer sufficient on their own. Businesses must adopt a layered approach to security, with a strong emphasis on data recovery and resilience.
The Dell EMC Cyber Recovery Vault offers a modern, forward-looking solution to the problem. Its combination of air-gapped security, immutable backups, and automated recovery positions it as a critical tool for businesses that want to ensure their data remains safe, even in the face of evolving cyber threats.
For organizations looking to build stronger cyber defenses and mitigate the risk of data loss from attacks, the Dell EMC Cyber Recovery Vault should be a top consideration in their data protection strategies.
You Might Also Like These:
How to Recover Your Cyber Power Computer from the Recovery Partition
The Recovery Process for Cybersecurity: A Comprehensive Guide
Recovery Mechanisms from Cyber Attacks
Mimecast Days of Data Recovery: Enhancing Cyber Resilience for Email
Ransomware Data Recovery in Los Angeles: A Guide by Nano Cyber