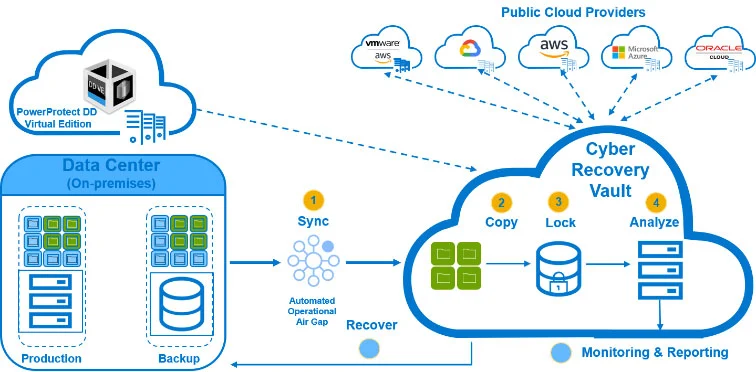
Dell Cyber Recovery Architecture, In today’s digital age, cybersecurity is no longer a luxury but a necessity. With the increasing frequency and sophistication of cyber threats, organizations must adopt robust strategies to safeguard their critical data and infrastructure. Dell Technologies, a leader in enterprise IT solutions, offers a comprehensive approach to data protection with its Dell Cyber Recovery Architecture.
Understanding Dell Cyber Recovery Architecture
Dell Cyber Recovery Architecture is a specialized framework designed to protect and recover critical business data from cyber-attacks, particularly ransomware. Unlike traditional backup solutions, this architecture focuses on isolating and safeguarding sensitive information to ensure business continuity and data integrity.
The architecture operates on three primary principles:
- Isolation: Dell Cyber Recovery Vault creates an air-gapped environment that isolates the backup from the production network. This reduces the risk of malware spreading from infected systems to the backup data.
- Immutability: The data stored within the Cyber Recovery Vault is immutable, meaning it cannot be altered or deleted by unauthorized users. This ensures the integrity of the backup, making it a reliable source for recovery.
- Intelligence: Dell leverages advanced analytics and machine learning to detect anomalies and potential threats within the backup data. This proactive approach helps in identifying potential risks before they impact the organization.
Key Components of Dell Cyber Recovery Architecture
- Cyber Recovery Vault: The cornerstone of the architecture, the vault is a secure, air-gapped environment that stores critical data in an isolated location. This vault significantly reduces the risk of cyber threats accessing the backup data.
- Policy Engine: It automates the management and orchestration of data movement between production environments and the vault. The policy engine ensures data is regularly updated and protected without manual intervention.
- Analytics Engine: Utilizing machine learning, this component continuously monitors data integrity and detects anomalies that could indicate a cyber threat. This early detection capability allows organizations to respond swiftly to potential risks.
- Recovery Tools: In the event of a cyber-attack, Dell Cyber Recovery Architecture provides tools and processes to restore data and resume operations quickly. The architecture supports flexible recovery options tailored to the organization’s needs.
Benefits of Dell Cyber Recovery Architecture
- Enhanced Security: By isolating and protecting critical data, Dell Cyber Recovery Architecture minimizes the attack surface and mitigates the impact of cyber threats.
- Rapid Recovery: Organizations can quickly restore their systems and data, minimizing downtime and ensuring business continuity.
- Regulatory Compliance: The architecture helps organizations meet stringent regulatory requirements for data protection and disaster recovery.
- Cost Efficiency: By preventing data loss and reducing recovery time, organizations can avoid the significant costs associated with prolonged downtime and data breaches.
Implementing Dell Cyber Recovery Architecture
Adopting Dell Cyber Recovery Architecture requires careful planning and execution. Organizations should start by assessing their current cybersecurity posture and identifying critical assets that need protection. Collaboration with Dell’s experts ensures a seamless integration of the architecture into existing IT environments.
Additionally, regular testing and updating of the recovery plan are crucial to ensure readiness in the face of evolving cyber threats. This continuous improvement approach ensures that the organization remains resilient and can adapt to new challenges.
Conclusion
In an era where cyber threats are a constant concern, Dell Cyber Recovery Architecture offers a reliable and innovative solution for protecting critical business data. Its unique combination of isolation, immutability, and intelligence provides organizations with the tools they need to safeguard their assets and ensure rapid recovery in the event of an attack. By implementing this architecture, businesses can enhance their cybersecurity posture, protect their reputation, and ensure long-term operational resilience.
You Might Also Like These: