Dell Cyber Recovery Solution, In today’s digital age, businesses face an ever-evolving landscape of cyber threats. From ransomware attacks to data breaches, the consequences of inadequate cybersecurity can be catastrophic. Organizations must prioritize not just prevention but also swift recovery to minimize downtime and financial loss. The Dell Cyber Recovery Solution offers a robust framework to safeguard businesses, ensuring that critical data remains protected and recoverable in the event of an attack.
The Growing Need for Cyber Recovery
The frequency and sophistication of cyberattacks are rising. Traditional backup solutions, while necessary, are no longer sufficient. Attackers have developed methods to target backups, encrypting or destroying them, leaving businesses unable to recover their essential data.
This is where the Dell Cyber Recovery Solution comes in. Unlike standard backup systems, this solution offers an isolated, secure environment that keeps a clean copy of critical data, shielded from cyber threats. It integrates seamlessly with existing infrastructure, offering a multi-layered defense strategy that includes prevention, detection, and recovery.
Key Features of Dell Cyber Recovery Solution
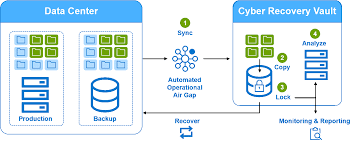
- Air-Gapped Vault: One of the standout features of Dell’s solution is its Cyber Recovery Vault. This vault provides an air-gapped, immutable environment for the most critical business data. By separating backup data from production environments, it ensures that even if attackers compromise the primary systems, the data within the vault remains untouched.
- Data Integrity and Analytics: The Dell Cyber Recovery Solution continuously monitors data integrity. Advanced analytics detect anomalies within the backup environment, alerting administrators to potential threats before they escalate. This allows businesses to identify compromised data early and take corrective actions.
- Automated Recovery Procedures: When disaster strikes, speed is of the essence. The solution offers automated recovery capabilities, ensuring businesses can quickly restore operations. In the event of a ransomware attack or other data compromise, the clean data stored in the vault can be restored to the production environment with minimal downtime.
- Regulatory Compliance: With the increasing complexity of data protection laws, compliance has become a top priority for many organizations. Dell’s solution helps businesses meet the stringent requirements of regulations like GDPR, HIPAA, and more. It ensures that sensitive data is stored, managed, and restored in compliance with industry standards.
- Seamless Integration: The Dell Cyber Recovery Solution integrates smoothly with other Dell Technologies infrastructure, such as PowerProtect Cyber Recovery and Dell EMC storage systems. This cohesive ecosystem allows businesses to bolster their cybersecurity defenses without overhauling their existing infrastructure.
How the Dell Cyber Recovery Solution Works
At its core, the Dell Cyber Recovery Solution creates a secure and isolated data vault, often referred to as the “Cyber Recovery Vault.” Data is periodically synchronized to the vault, but the synchronization is done in a way that ensures the vault remains protected from malicious threats within the primary network.
The process typically involves:
- Data Synchronization: Data from the production environment is replicated to the vault in intervals, ensuring that an up-to-date copy is always available.
- Isolation and Air-Gapping: The vault is kept isolated from the primary environment, making it inaccessible to any compromised systems or malware in the main network.
- Automated Workflows: Pre-configured workflows allow for quick detection and restoration of clean data, enabling rapid recovery post-incident.
- Forensic Analysis: In addition to recovery, the Dell solution allows businesses to investigate the attack in a controlled environment, helping them understand the threat and how to prevent similar incidents in the future.
Why Choose Dell for Cyber Recovery?
Dell Technologies has established itself as a leader in data protection and cybersecurity. The Dell Cyber Recovery Solution is built on years of expertise and innovation, providing businesses with a trusted and proven platform for data recovery.
- Industry-Leading Technology: Dell is known for its cutting-edge infrastructure solutions, and the Cyber Recovery Solution is no exception. It leverages advanced hardware and software to offer comprehensive protection against modern threats.
- Expert Support: Dell provides ongoing support and professional services to help businesses implement and manage their cyber recovery strategy effectively.
- Scalability: As businesses grow, so do their data protection needs. The Dell solution is scalable, allowing companies to expand their cyber recovery capabilities as their operations and data increase.
Conclusion
In the face of increasing cyber threats, businesses must go beyond traditional cybersecurity measures. The Dell Cyber Recovery Solution provides a critical layer of protection, ensuring that vital data remains secure and recoverable. By isolating backup data in an air-gapped vault, offering automated recovery, and ensuring compliance with regulatory requirements, Dell’s solution gives organizations peace of mind in an uncertain digital world.
Incorporating Dell’s advanced cyber recovery solution into a broader cybersecurity strategy is not just a smart move—it’s essential for businesses aiming to stay resilient in today’s increasingly hostile cyber environment.
You Might Also Like These:
Cyber Insurance Recovery: Navigating the Road to Resilience
Cyber Recovery Services: Safeguarding Your Business in the Digital Age
Credit Recovery at Agora Cyber: A Path to Academic Success
The Importance of Cyber Security Logos in Disaster Recovery Planning