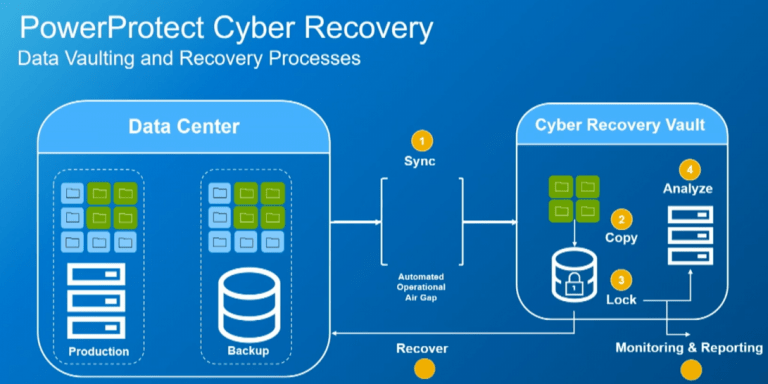
Dell Emc PowerProtect Cyber Recovery, In today’s digital landscape, organizations face an increasing number of cyber threats that can jeopardize their critical data. To combat these risks, businesses must adopt robust data protection strategies. Dell EMC PowerProtect Cyber Recovery is a powerful solution designed to help organizations safeguard their data against cyber threats, ensuring resilience and rapid recovery in the event of an incident.
Understanding Cyber Recovery
Cyber recovery refers to the processes and technologies that allow organizations to recover their data and systems after a cyber attack or data breach. With cyber incidents becoming more sophisticated, traditional backup methods are often insufficient. Organizations need solutions that not only protect data but also ensure that it can be quickly restored without compromising security.
Key Features of Dell EMC PowerProtect Cyber Recovery
- Immutable Backups: One of the standout features of Dell EMC PowerProtect Cyber Recovery is its ability to create immutable backups. This means that once data is backed up, it cannot be altered or deleted until a specified retention period expires. This immutability helps protect against ransomware attacks, as cybercriminals are unable to encrypt or delete backup data.
- Isolation and Security: PowerProtect Cyber Recovery provides a secure and isolated environment for backup data. This air-gapped approach minimizes the risk of malware or ransomware accessing backup files, ensuring that recovery data remains safe and intact.
- Rapid Recovery: In the event of a cyber incident, speed is critical. Dell EMC PowerProtect Cyber Recovery facilitates rapid recovery of data and applications, allowing organizations to minimize downtime and maintain business continuity. The solution’s streamlined recovery processes ensure that data can be restored quickly and efficiently.
- Automated Testing: Regular testing of recovery processes is essential to ensure effectiveness. PowerProtect Cyber Recovery includes automated testing features that allow organizations to validate their backup and recovery strategies without disrupting ongoing operations. This proactive approach helps identify potential issues before they become critical problems.
- Compliance and Reporting: For organizations in regulated industries, compliance is a top priority. Dell EMC PowerProtect Cyber Recovery offers comprehensive reporting and auditing capabilities that help organizations demonstrate compliance with various regulatory standards. This transparency is crucial for maintaining trust with customers and stakeholders.
Benefits of Implementing Dell EMC PowerProtect Cyber Recovery
- Enhanced Data Security: With its advanced features and robust security measures, PowerProtect Cyber Recovery significantly enhances an organization’s data protection strategy, reducing the risk of data loss due to cyber threats.
- Improved Business Continuity: The ability to quickly recover from cyber incidents ensures that businesses can continue operations with minimal disruption, protecting revenue and customer satisfaction.
- Scalability: Dell EMC PowerProtect Cyber Recovery is designed to scale with the organization’s needs, making it suitable for businesses of all sizes, from small enterprises to large corporations.
- Cost Efficiency: By reducing downtime and the potential costs associated with data breaches, PowerProtect Cyber Recovery can lead to significant cost savings over time.
Conclusion
In an era where cyber threats are ever-evolving, the need for comprehensive data protection solutions has never been more critical. Dell EMC PowerProtect Cyber Recovery stands out as a robust solution that not only protects organizations from cyber risks but also ensures rapid recovery and business continuity. By investing in this technology, businesses can enhance their resilience against cyber threats, safeguarding their data and maintaining trust with their customers. As cyber recovery strategies continue to evolve, adopting solutions like Dell EMC PowerProtect Cyber Recovery is a crucial step toward securing the future of any organization.
You Might Also Like These:
cyber attack disaster recovery plan template
cyber security recovery plan sample