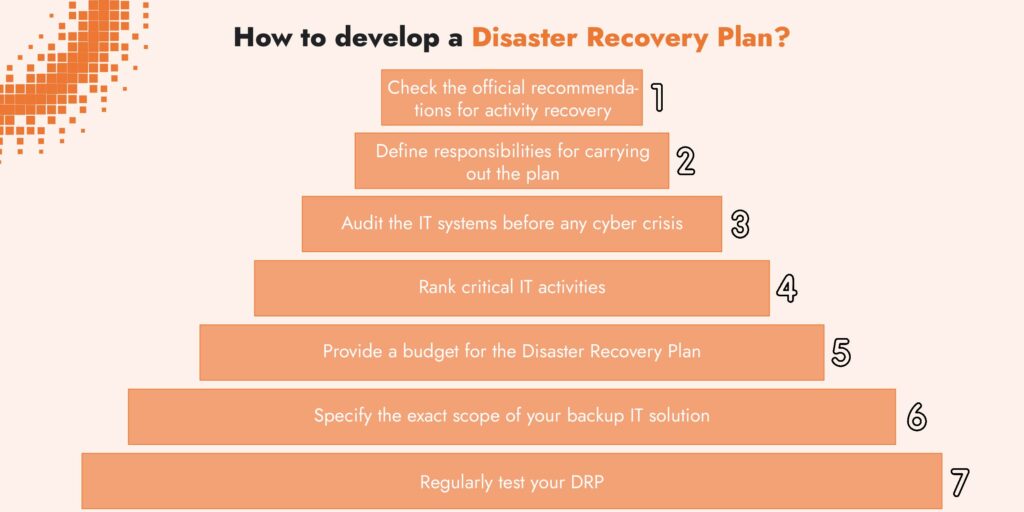
It Cyber Attack Recovery Plan, In today’s digital landscape, the threat of cyber attacks looms large over organizations of all sizes. As businesses increasingly rely on technology for their operations, the need for a robust IT cyber attack recovery plan has become paramount. Such a plan not only minimizes damage during an incident but also ensures a swift return to normal operations. Here’s how to develop an effective cyber attack recovery plan.
Understanding Cyber Attacks
Cyber attacks can take many forms, including ransomware, phishing, denial of service (DoS) attacks, and data breaches. Each of these attacks can disrupt business operations, compromise sensitive data, and incur significant financial losses. Therefore, a proactive approach to cybersecurity is essential.
Key Components of an IT Cyber Attack Recovery Plan
1. Risk Assessment
Before crafting a recovery plan, organizations must conduct a comprehensive risk assessment. Identify potential vulnerabilities in your IT infrastructure and evaluate the likelihood and impact of various types of cyber attacks. This assessment will inform the development of your recovery strategies.
2. Incident Response Team
Establish a dedicated incident response team responsible for managing cyber incidents. This team should include IT staff, cybersecurity experts, and representatives from key business units. Clearly define roles and responsibilities to ensure a coordinated response during an attack.
3. Data Backup and Recovery
Regular data backups are a cornerstone of any recovery plan. Ensure that critical data is backed up frequently and stored securely, preferably in multiple locations (both on-site and off-site). Implement a tested process for data recovery to minimize downtime in the event of a cyber attack.
4. Communication Plan
Develop a communication strategy that outlines how information will be shared internally and externally during and after an attack. This includes notifying stakeholders, customers, and regulatory bodies as required. Clear communication can help manage reputational risk and maintain trust.
5. Recovery Procedures
Outline step-by-step procedures for recovering from a cyber attack. This should include:
- Containment: Steps to isolate affected systems and prevent further damage.
- Eradication: Procedures to remove the threat from your environment.
- Recovery: Detailed plans for restoring systems and data, including testing to ensure everything is functioning correctly.
- Post-Incident Review: Analyze the incident to identify lessons learned and areas for improvement.
6. Training and Awareness
Regular training and awareness programs are essential for all employees. Conduct drills simulating cyber attack scenarios to ensure that everyone knows their role in the recovery process. Foster a culture of cybersecurity awareness to help prevent attacks from occurring in the first place.
7. Continuous Improvement
An IT cyber attack recovery plan is not a static document. It should be reviewed and updated regularly to account for new threats, changes in technology, and lessons learned from previous incidents. Incorporate feedback from team members and stakeholders to refine your strategies.
Conclusion
A well-crafted IT cyber attack recovery plan is crucial for any organization seeking to protect itself against the growing threat of cyber attacks. By understanding potential risks, establishing a dedicated response team, implementing robust backup procedures, and fostering a culture of cybersecurity, businesses can minimize damage and recover more quickly in the event of an attack. Remember, the best defense against cyber threats is a proactive and prepared organization.
You Might Also Like These: