Power Protect Cyber Recovery, In an era where cyber threats are evolving at an alarming pace, ensuring the security of critical data has never been more important. One of the most effective solutions to combat these threats is Power Protect Cyber Recovery, a comprehensive strategy designed to safeguard sensitive information and ensure business continuity in the face of cyberattacks.
Understanding Power Protect Cyber Recovery
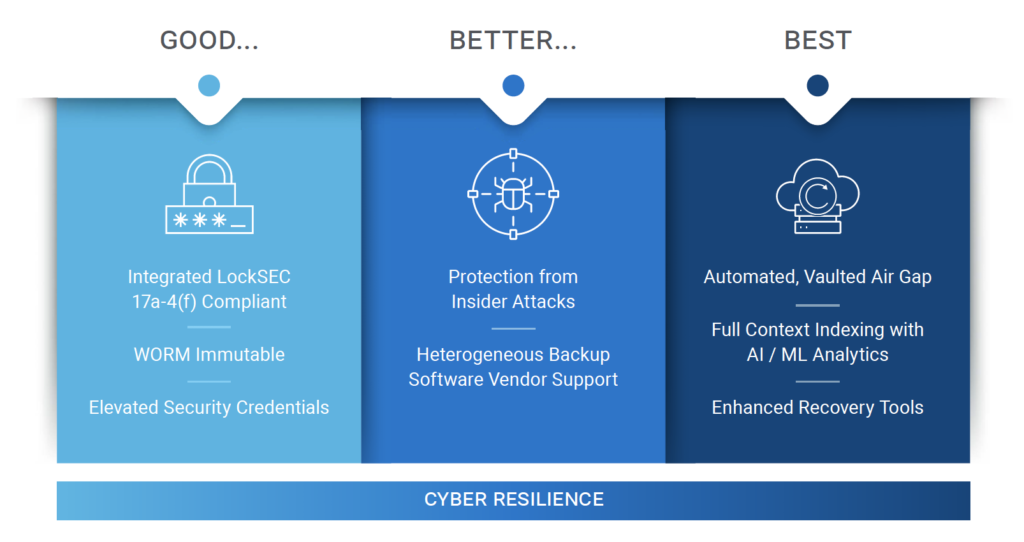
Power Protect Cyber Recovery refers to a suite of technologies and practices aimed at protecting an organization’s data from cyber threats such as ransomware, malware, and other forms of cyberattacks. It goes beyond traditional data backup solutions by focusing on resilience and rapid recovery, ensuring that businesses can quickly bounce back from any disruption.
Key Features of Power Protect Cyber Recovery
- Isolated Recovery Environment (IRE): This feature creates a secure, air-gapped environment where critical data is stored separately from the primary network. This isolation prevents attackers from accessing or compromising the backup data, even if the main network is breached.
- Immutable Backups: Power Protect Cyber Recovery employs immutable storage, meaning that once data is written, it cannot be altered or deleted. This ensures the integrity of the backup data, making it reliable for recovery purposes.
- Automated Data Recovery: In the event of an attack, the system can quickly identify the last known good state of the data and initiate an automated recovery process. This minimizes downtime and helps maintain business continuity.
- Advanced Threat Detection: The solution includes advanced analytics and machine learning algorithms to detect unusual patterns or potential threats in the backup data. Early detection allows for quicker response and mitigation.
Benefits of Power Protect Cyber Recovery
- Enhanced Security: By isolating and securing backup data, organizations significantly reduce the risk of data loss or corruption due to cyberattacks.
- Business Continuity: Quick recovery times mean that businesses can continue operations with minimal disruption, even after a significant cyber event.
- Compliance and Governance: Many industries have strict regulations regarding data protection and recovery. Power Protect Cyber Recovery helps organizations meet these requirements by providing reliable and secure data recovery solutions.
- Cost Savings: While the initial investment in cyber recovery solutions may be significant, the long-term savings from avoiding downtime, data loss, and potential regulatory fines are substantial.
Implementing Power Protect Cyber Recovery
Implementing a robust Power Protect Cyber Recovery strategy involves several steps:
- Assessment: Organizations need to assess their current cyber resilience capabilities and identify critical data and systems that require protection.
- Planning: Develop a comprehensive recovery plan that outlines the processes, technologies, and personnel involved in the recovery process.
- Deployment: Deploy the necessary hardware and software solutions, ensuring that they are correctly configured to provide maximum protection and recovery capabilities.
- Testing and Maintenance: Regularly test the recovery processes to ensure they work as expected. Update and maintain the systems to keep up with evolving cyber threats.
Conclusion
In today’s digital landscape, the threat of cyberattacks is omnipresent. Power Protect Cyber Recovery provides organizations with the tools and strategies necessary to protect their critical data, maintain business continuity, and recover quickly from cyber incidents. By investing in this advanced recovery solution, businesses can enhance their resilience against cyber threats and ensure their long-term success.
You Might Also Like These: