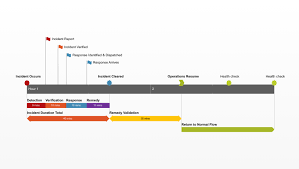
Introduction
Recovery Timeline Cyber Incident, In today’s digital landscape, the likelihood of facing a cyber incident is increasingly high for businesses and organizations of all sizes. Whether it’s a data breach, ransomware attack, or malware infection, the aftermath of such an incident can be devastating. The path to full recovery can be long and complex. Understanding the recovery timeline for a cyber incident is crucial for minimizing damage, restoring systems, and rebuilding trust.
This article provides an in-depth look at the stages of recovery, highlighting the importance of each step and offering guidance on how organizations can navigate them effectively.
Phase 1: Immediate Response (0–24 Hours)
The first 24 hours following a cyber incident are critical. This is the stage when quick action can prevent further damage and begin the recovery process. During this time, the focus should be on containing the incident and assessing the extent of the breach. Key steps include:
- Incident Detection – Identifying the breach or attack as early as possible is essential. This can be through intrusion detection systems, antivirus alerts, or abnormal activity spotted by employees.
- Initial Containment – Once the incident is detected, efforts should be made to stop the attack from spreading. This could involve isolating affected systems, disabling user accounts, or shutting down compromised networks.
- Communication Plan Activation – Informing internal teams and stakeholders about the incident is crucial. At this stage, it’s also important to consult legal and regulatory teams to understand reporting requirements, especially if sensitive data is involved.
Phase 2: Initial Recovery (24–72 Hours)
Once the immediate threat is contained, the next phase involves beginning to restore affected systems and data. This stage typically lasts from 24 to 72 hours and focuses on understanding the full scope of the incident.
- Forensic Investigation – Conducting a forensic analysis is vital to determine the origin, scope, and impact of the attack. This analysis helps identify vulnerabilities and assists in deciding what systems need to be restored.
- Backup Restoration – If the incident has corrupted or deleted data, backups are used to restore the compromised information. Ideally, the organization has secured, up-to-date backups that haven’t been affected by the cyberattack.
- Incident Reporting – Depending on the type of breach, organizations may be required to report the incident to regulatory bodies or inform affected customers. Clear and transparent communication is key to maintaining trust.
Phase 3: System Recovery and Stability (3–7 Days)
After the initial containment and data restoration, the focus shifts to full system recovery and ensuring long-term stability. This phase typically spans 3 to 7 days and includes:
- System Patching – Fixing the vulnerabilities that led to the incident is crucial. This can involve applying software patches, updating firewalls, and tightening access controls.
- Data Integrity Check – Once systems are back online, conducting data integrity checks ensures that no hidden malware remains and that data hasn’t been altered by the attack.
- User Credential Reset – As a precautionary measure, it’s essential to reset all compromised user credentials and implement stricter access controls.
- Monitoring Systems – Enhanced monitoring of networks, systems, and applications should be in place during this time to ensure no follow-up attacks or lingering threats go unnoticed.
Phase 4: Full Recovery and Post-Incident Analysis (7–30 Days)
In the days and weeks following the cyber incident, organizations should focus on reinforcing their defenses and learning from the attack. This stage may take anywhere from a week to a month, depending on the complexity of the attack.
- Full Restoration of Services – Ensure all business-critical services are fully restored and operational. This may include reinstalling operating systems or software to remove any lingering threats.
- Post-Incident Review – Conducting a full post-incident review helps organizations identify what went wrong, what worked, and how they can improve. This can involve gathering input from IT teams, management, and external cybersecurity experts.
- Employee Training – Since human error is often a factor in cyber incidents, reinforcing cybersecurity training is vital. This can involve new protocols for phishing detection, password management, or secure file handling.
- Implementing Lessons Learned – The final step in the recovery timeline is to apply the lessons learned from the incident. This may lead to changes in security policies, incident response plans, and overall cybersecurity strategy.
Phase 5: Long-Term Strategy and Prevention (30 Days and Beyond)
The final phase in the recovery timeline is focused on long-term resilience. Once the immediate threat is resolved and systems are restored, organizations should reassess their cybersecurity posture and implement improvements to prevent future incidents.
- Updating Incident Response Plan – Revise and improve your incident response plan based on the lessons learned from the incident. This ensures the organization is better prepared for future cyberattacks.
- Advanced Security Measures – Consider adopting more advanced cybersecurity solutions like multi-factor authentication (MFA), endpoint detection and response (EDR), and Security Information and Event Management (SIEM) systems.
- Continuous Monitoring and Testing – Establish regular system audits and vulnerability assessments to identify and fix weaknesses before they can be exploited.
- Building a Culture of Security – Foster a culture where cybersecurity is a priority. Ensure that all employees understand their role in protecting the organization and that they have the necessary tools to do so.
Conclusion
Recovering from a cyber incident is not just about restoring systems; it’s about learning from the experience and strengthening your organization’s defenses. The recovery timeline from a cyber incident is multifaceted, spanning from immediate response in the first 24 hours to long-term strategies for resilience. By understanding each phase and implementing best practices at every stage, businesses can minimize damage, rebuild trust, and emerge stronger after an attack.
Having a clear, well-tested incident response plan is key to shortening the recovery timeline and ensuring business continuity after a cyber incident.
You Might Also Like These:
Cyber Attack Recovery: A Comprehensive Guide to Protecting Your Business
Cyber Security Disaster Recovery Plan: An Essential Guide for Businesses
Mac Data Recovery Cyber Monday: The Ultimate Guide to Restoring Your Lost Files at a Discount
Phases of a Recovery from a Cyber Attack: A Comprehensive Guide