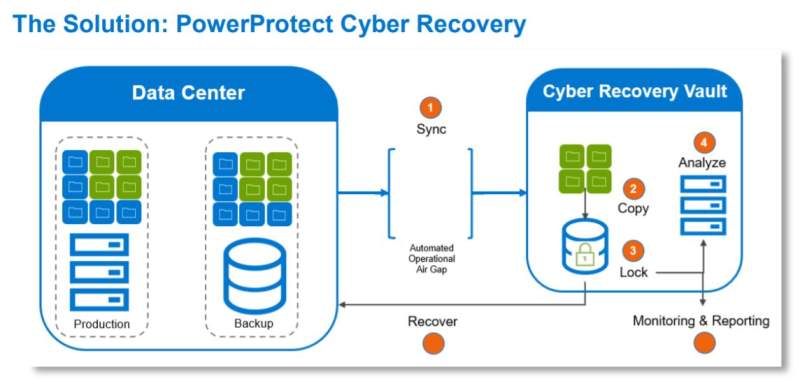
Cyber Recovery Automation, As cyber threats continue to evolve, organizations must adopt robust strategies to ensure their data and systems remain secure and resilient. One of the most effective strategies emerging in recent years is cyber recovery automation. This approach not only streamlines the recovery process but also enhances an organization’s ability to respond to cyber incidents swiftly and efficiently.
Understanding Cyber Recovery Automation
Cyber recovery automation refers to the use of technology and automated processes to manage and execute recovery operations in the event of a cyber incident. This includes automated backups, rapid data restoration, and systematic processes to ensure business continuity. By integrating automation into cyber recovery plans, organizations can reduce downtime, minimize human error, and recover critical systems faster.
Key Benefits of Cyber Recovery Automation
- Speed and Efficiency: One of the primary advantages of automation in cyber recovery is speed. Automated recovery processes can drastically reduce the time required to restore systems and data. With automated solutions in place, organizations can recover from cyber incidents in hours rather than days, minimizing operational disruption.
- Reduced Human Error: Manual recovery processes are often prone to errors, especially under pressure. Automation helps to eliminate human error by standardizing recovery procedures and executing them consistently. This reliability is crucial during a crisis when quick and accurate decision-making is essential.
- Enhanced Data Integrity: Cyber recovery automation ensures that data is consistently backed up and verified. Automated solutions can regularly check the integrity of backups and perform necessary updates without manual intervention. This proactive approach protects against data corruption and ensures that recovery points are reliable.
- Cost Savings: By reducing downtime and the need for extensive manual intervention, cyber recovery automation can lead to significant cost savings. Organizations can allocate resources more effectively, focusing on strategic initiatives rather than firefighting after a cyber incident.
- Scalability: As organizations grow, their data and systems become increasingly complex. Cyber recovery automation provides a scalable solution that can adapt to changing environments. Automated processes can be easily adjusted to accommodate new systems, applications, and data types, ensuring that recovery plans remain effective as the organization evolves.
Implementing Cyber Recovery Automation
To successfully implement cyber recovery automation, organizations should consider the following steps:
- Assess Current Infrastructure: Begin by evaluating existing backup and recovery processes. Identify gaps in current capabilities and determine how automation can enhance these processes.
- Choose the Right Tools: Select automation tools and platforms that align with your organization’s specific needs. Consider factors such as integration capabilities, ease of use, and support for existing technologies.
- Develop a Comprehensive Plan: Create a detailed cyber recovery plan that incorporates automation. This plan should outline roles, responsibilities, and procedures for automated recovery processes.
- Regular Testing: Conduct regular testing of automated recovery processes to ensure they work as intended. Simulated cyber incidents can help identify weaknesses and refine recovery strategies.
- Continuous Improvement: Cyber threats are constantly evolving, and so should your recovery strategies. Regularly review and update your cyber recovery automation processes to adapt to new threats and technologies.
Conclusion
As cyber threats continue to pose significant risks to organizations of all sizes, adopting cyber recovery automation is no longer optional; it is a necessity. By leveraging automated recovery processes, organizations can enhance their resilience against cyber incidents, reduce recovery times, and ultimately protect their critical data and systems. Embracing this technology not only prepares organizations for the challenges of today but also positions them for a more secure future in the digital landscape.
You Might Also Like These:
cyber security recovery plan template