The Main Purpose Of Cyber Incident Recovery Is To Restore System To __., In today’s digital landscape, where businesses heavily rely on technology and interconnected systems, the threat of cyber incidents looms larger than ever. Cyber incidents can range from data breaches and ransomware attacks to more sophisticated forms of cyber warfare. Consequently, organizations must have robust cyber incident recovery plans in place. The main purpose of cyber incident recovery is to restore systems to normal operations, ensuring minimal disruption to business functions and safeguarding critical data.
Understanding Cyber Incident Recovery
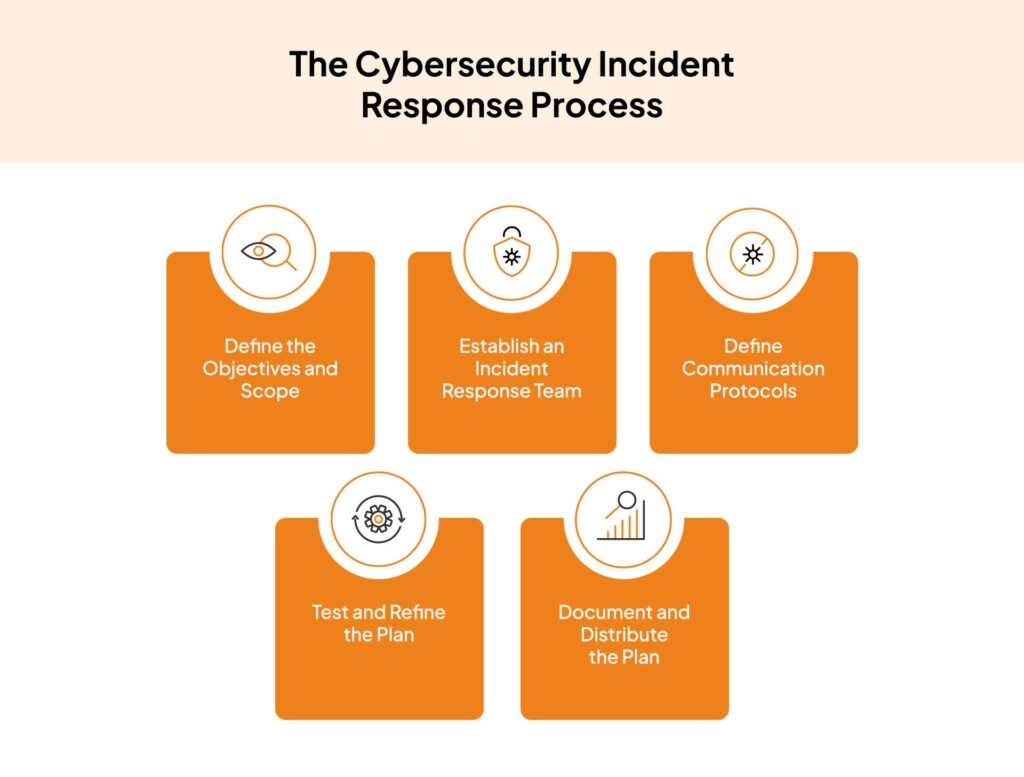
Cyber incident recovery refers to the processes and strategies employed to respond to and recover from cyber threats. This involves several critical components:
- Preparation: Before an incident occurs, organizations should develop comprehensive recovery plans that outline specific roles, responsibilities, and procedures. This preparation includes regular training and simulations to ensure that all staff are familiar with their roles in the event of a cyber incident.
- Detection and Analysis: Once a cyber incident is detected, it is essential to analyze the scope and impact of the incident. This analysis helps determine the appropriate recovery actions and prioritizes the systems that require immediate attention.
- Containment: The next step involves containing the incident to prevent further damage. This may include isolating affected systems, blocking malicious traffic, and implementing temporary security measures.
- Eradication: After containment, organizations must eradicate the root cause of the incident. This may involve removing malware, addressing vulnerabilities, and implementing patches to prevent future attacks.
- Recovery: The heart of cyber incident recovery is the restoration of systems to normal operations. This may include restoring data from backups, reconfiguring systems, and validating that the environment is secure before bringing systems back online.
- Post-Incident Review: After recovery, organizations should conduct a thorough review of the incident. This includes documenting lessons learned, assessing the effectiveness of the recovery plan, and making necessary adjustments to improve future responses.
The Importance of Restoring Systems to Normal Operations
Restoring systems to normal operations is crucial for several reasons:
- Business Continuity: A swift recovery ensures that businesses can continue to operate with minimal downtime. This is particularly vital for customer-facing services, as prolonged disruptions can lead to lost revenue and damaged reputations.
- Data Integrity: By restoring systems and data promptly, organizations can minimize the risk of data loss or corruption. Ensuring that data remains intact is essential for regulatory compliance and maintaining customer trust.
- Security Posture: The recovery process often involves reinforcing security measures and addressing vulnerabilities that were exploited during the incident. This proactive approach strengthens the organization’s overall cybersecurity posture.
- Regulatory Compliance: Many industries are governed by regulations that mandate specific recovery timeframes. Meeting these requirements is essential for avoiding penalties and maintaining operational licenses.
Conclusion
In conclusion, the main purpose of cyber incident recovery is to restore systems to normal operations. This not only facilitates business continuity but also enhances data integrity and security. By implementing a comprehensive recovery plan, organizations can effectively mitigate the impacts of cyber incidents and position themselves for a more resilient future. As cyber threats continue to evolve, prioritizing recovery strategies will be essential for safeguarding both organizational assets and customer trust.
You Might Also Like These: