Nist Cyber Event Recovery Guide, Understanding the NIST Cyber Event Recovery Guide: A Blueprint for Resilience, In today’s digitally driven world, cyber threats are an ever-present concern for organizations. The rapid evolution of these threats necessitates robust and well-structured strategies to handle cyber incidents. Effective practices for cyber incident response and recovery are crucial in minimizing damage, preserving organizational integrity, and ensuring business continuity. Here’s a detailed exploration of these practices:
1. Developing a Comprehensive Incident Response Plan
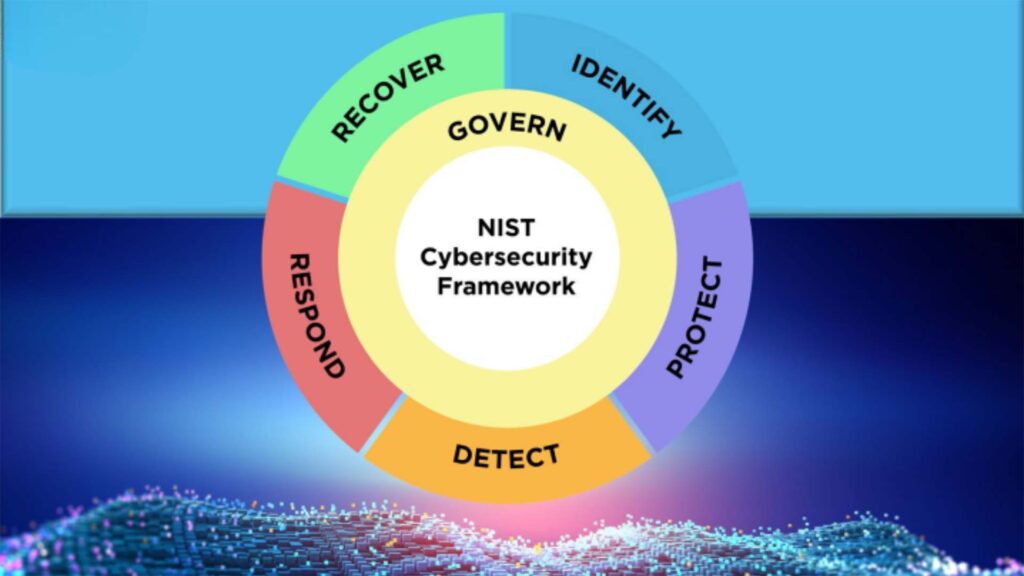
An effective incident response plan (IRP) is the foundation of any cyber defense strategy. This plan should clearly outline the steps to be taken when a cyber incident occurs, define roles and responsibilities, and establish communication protocols. Key components of a robust IRP include:
- Preparation: Establish a response team, conduct regular training, and perform threat simulations.
- Identification: Detect and verify the incident using monitoring tools and threat intelligence.
- Containment: Limit the spread of the threat by isolating affected systems.
- Eradication: Remove the root cause of the incident from the system.
- Recovery: Restore systems and data from backups, ensuring normal operations.
- Lessons Learned: Post-incident review to improve future responses.
2. Regular Training and Drills
Regular training for the incident response team and organization-wide awareness programs are vital. Employees should be familiar with the IRP and know their role in mitigating cyber incidents. Drills and simulations of different attack scenarios help the team practice their response in a controlled environment, highlighting areas that need improvement.
3. Leveraging Advanced Threat Detection Tools
Utilizing sophisticated threat detection tools can significantly enhance an organization’s ability to identify and respond to cyber threats quickly. Tools such as Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS), and endpoint detection and response (EDR) solutions provide real-time monitoring and alerting, enabling swift action to contain threats.
4. Establishing Clear Communication Channels
Effective communication is critical during a cyber incident. Establishing clear communication channels ensures that relevant information is shared promptly among internal teams, stakeholders, and possibly external entities like law enforcement or regulatory bodies. Transparency in communication helps maintain trust with customers and partners during and after the incident.
5. Implementing Backup and Recovery Solutions
Regularly updated and tested backup solutions are essential for quick recovery from a cyber incident. Data should be backed up frequently, with copies stored securely off-site or in the cloud. In the event of a ransomware attack or data breach, having reliable backups enables the organization to restore its operations with minimal data loss.
6. Post-Incident Analysis and Continuous Improvement
After resolving a cyber incident, a detailed post-mortem analysis is crucial. This review should assess the effectiveness of the response, identify gaps in the IRP, and recommend enhancements. Continuous improvement ensures that the organization is better prepared for future incidents, making it a key component of an effective incident response strategy.
Conclusion
Effective practices for cyber incident response and recovery are essential to safeguarding an organization’s digital assets and reputation. By developing a comprehensive IRP, conducting regular training, utilizing advanced detection tools, establishing clear communication, and focusing on continuous improvement, organizations can enhance their resilience against cyber threats. Implementing these practices not only minimizes the impact of cyber incidents but also fosters a proactive security culture within the organization.
You Might Also Like These: