What Is Cyber Incident Recovery, In today’s digital landscape, the threat of cyber incidents looms large over organizations of all sizes. Whether it’s a data breach, ransomware attack, or any other form of cyber disruption, the need for a robust recovery strategy is critical. This brings us to an essential concept in cybersecurity: cyber incident recovery.
Understanding Cyber Incident Recovery
Cyber incident recovery refers to the processes and strategies that organizations implement to recover from a cybersecurity incident and restore normal operations. This involves not just the technical aspects of recovering data and systems but also the management of communication, compliance, and risk mitigation.
The Importance of Cyber Incident Recovery
The stakes are high when a cyber incident occurs. Organizations can face significant financial losses, reputational damage, and regulatory penalties. A well-defined incident recovery plan enables businesses to:
- Minimize Downtime: Swift recovery actions help in reducing the operational downtime caused by cyber incidents.
- Safeguard Data Integrity: Effective recovery strategies ensure that data integrity is maintained, protecting sensitive information from corruption or loss.
- Restore Business Continuity: Recovery plans allow organizations to return to normal operations as quickly as possible, minimizing the impact on customers and stakeholders.
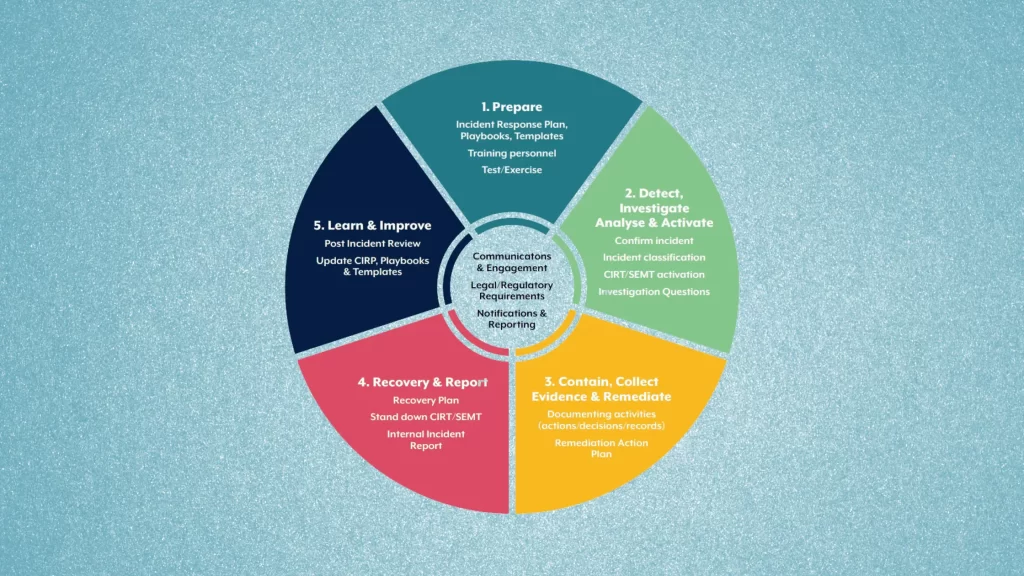
Key Components of a Cyber Incident Recovery Plan
A comprehensive cyber incident recovery plan typically includes several key components:
- Preparation: Organizations must first assess their vulnerabilities and establish a baseline for incident response. This can involve conducting regular risk assessments and training staff on security protocols.
- Detection and Analysis: Quick identification of an incident is crucial. Organizations should implement monitoring systems to detect anomalies and establish procedures for incident classification and severity assessment.
- Containment: Once an incident is detected, immediate containment measures must be activated to prevent further damage. This may involve isolating affected systems and blocking malicious traffic.
- Eradication and Recovery: After containment, organizations should identify the root cause of the incident and remove any threats from their environment. This phase also includes restoring systems from backups and ensuring that all software is up to date.
- Post-Incident Review: After recovery, a thorough review should be conducted to analyze the incident and response effectiveness. This review helps identify lessons learned and opportunities for improvement in future incident responses.
Best Practices for Cyber Incident Recovery
- Develop a Response Team: Establish a dedicated team responsible for incident response and recovery. This team should include members from various departments, such as IT, legal, communications, and management.
- Regular Testing and Drills: Conduct regular tests of the recovery plan to ensure all team members are familiar with their roles. Simulation exercises can help identify gaps in the plan and improve response times.
- Maintain Backups: Regularly back up critical data and systems. Ensure that backups are stored securely and tested frequently to verify their integrity.
- Communicate Clearly: Effective communication is essential during a cyber incident. Develop a communication plan to inform stakeholders, employees, and customers about the incident and the recovery process.
- Stay Informed: Cyber threats evolve rapidly. Organizations should stay informed about the latest threats and vulnerabilities to adjust their recovery plans accordingly.
Conclusion
In an era where cyber threats are increasingly sophisticated and prevalent, understanding what cyber incident recovery entails is vital for all organizations. By developing a robust recovery strategy, businesses can not only mitigate the impact of cyber incidents but also enhance their resilience against future threats. Ultimately, effective cyber incident recovery is a critical component of an organization’s overall cybersecurity posture, ensuring business continuity and protecting valuable assets.
You Might Also Like These: