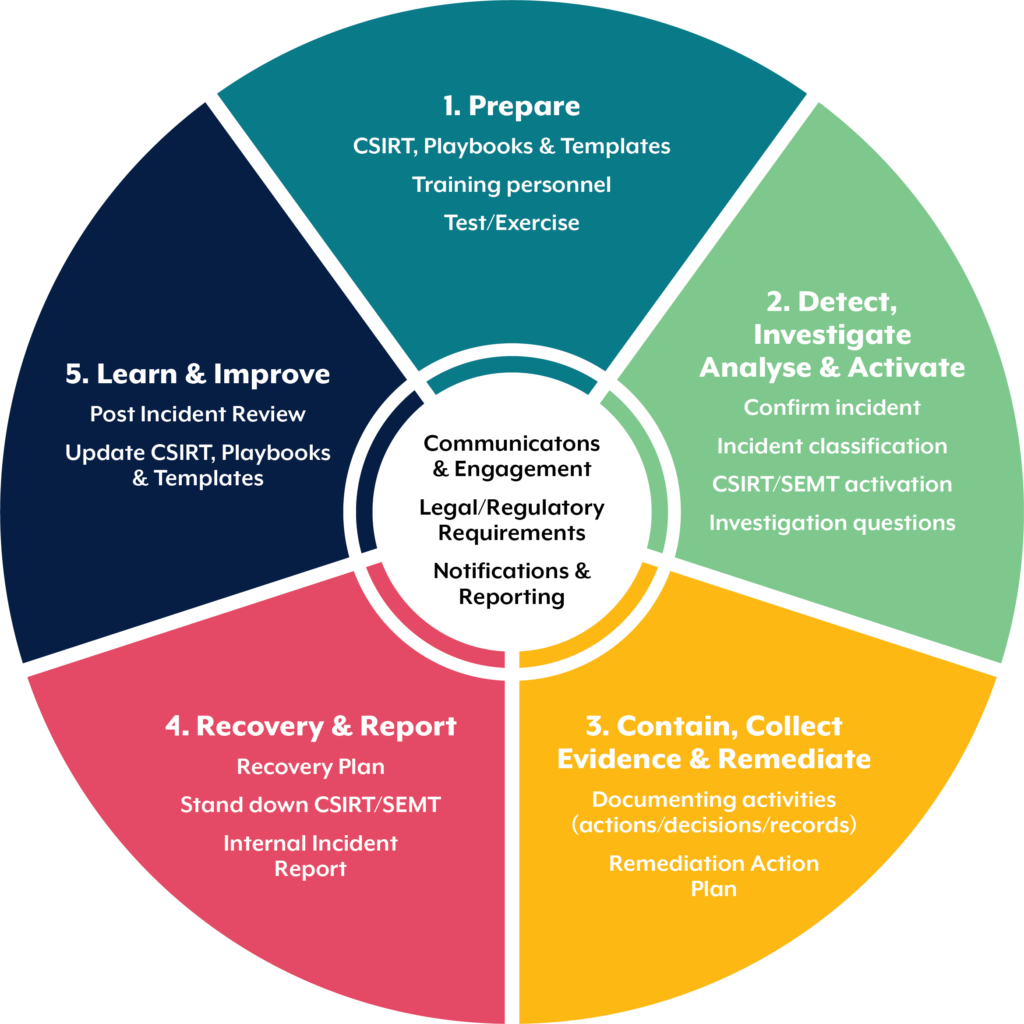
Whiy Is A Cyber Recovery Plan Important, In an age where digital transformation is accelerating at an unprecedented pace, businesses are becoming increasingly reliant on technology. However, this reliance also brings heightened risks, particularly in the realm of cybersecurity. A cyber recovery plan is not just a safety net; it is a crucial component of an organization’s overall risk management strategy. Here, we explore the importance of having a cyber recovery plan in place.
1. Minimizing Downtime
One of the most immediate impacts of a cyberattack, such as a ransomware incident, is operational downtime. Businesses can lose significant revenue for every hour they are offline. A well-defined cyber recovery plan helps minimize this downtime by providing a clear framework for response. It outlines the steps to restore systems and data quickly, allowing operations to resume as swiftly as possible.
2. Protecting Critical Data
Data is the lifeblood of any organization. Whether it’s customer information, financial records, or intellectual property, losing this data can have devastating consequences. A cyber recovery plan involves regular backups and data recovery strategies, ensuring that critical information can be restored with minimal loss. This protection is essential not only for business continuity but also for maintaining customer trust and regulatory compliance.
3. Enhancing Incident Response
A cyber recovery plan is part of a broader incident response strategy. By outlining specific roles, responsibilities, and actions, organizations can respond more effectively to incidents. This includes identifying the source of the breach, containing the damage, and communicating with stakeholders. A swift and organized response can significantly mitigate the impact of a cyber event.
4. Reducing Financial Impact
The financial implications of a cyber incident can be staggering. Costs can include lost revenue, recovery expenses, legal fees, and potential regulatory fines. By having a cyber recovery plan in place, organizations can significantly reduce these costs. Quick recovery translates into less revenue lost and fewer resources spent on mitigating the attack’s effects.
5. Maintaining Business Reputation
In today’s interconnected world, news of a cyber incident spreads rapidly. A company’s reputation can suffer long-lasting damage if it is perceived as unable to protect its data. A robust cyber recovery plan demonstrates to customers, partners, and stakeholders that the organization takes cybersecurity seriously and is prepared to handle incidents effectively. This can enhance trust and foster customer loyalty.
6. Ensuring Regulatory Compliance
With the increasing number of regulations governing data protection and privacy, organizations must comply with various legal requirements. A cyber recovery plan not only helps in recovering from incidents but also ensures that the organization adheres to compliance standards. This can help avoid hefty fines and legal repercussions associated with data breaches.
7. Preparing for Future Threats
Cyber threats are constantly evolving. A cyber recovery plan is not a static document; it should be regularly updated to reflect new threats and changes in the business environment. By regularly testing and refining the plan, organizations can stay one step ahead of potential attackers and ensure that they are prepared for future incidents.
Conclusion
In conclusion, a cyber recovery plan is a vital investment for any organization that relies on technology. It minimizes downtime, protects critical data, enhances incident response, reduces financial impact, maintains business reputation, ensures regulatory compliance, and prepares for future threats. As cyber threats continue to evolve, the importance of having a well-defined and tested recovery plan cannot be overstated. Organizations that prioritize cyber recovery planning are better positioned to navigate the complex digital landscape and protect their assets in the face of adversity.
You Might Also Like These: